Forensics
What App is on Fire?

Open chall.E01 with FTK Imager
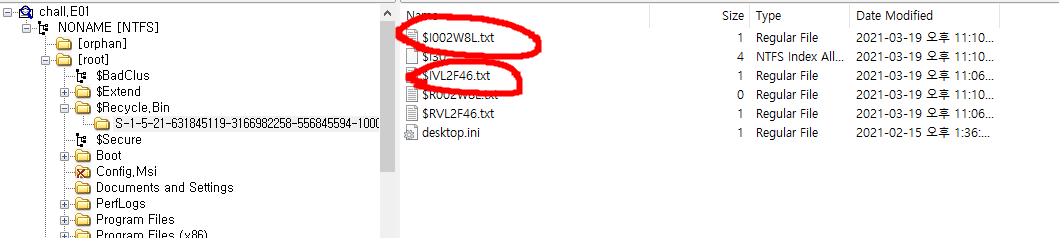
In Recycle.Bin, i found meaningful data in two txt files.

and
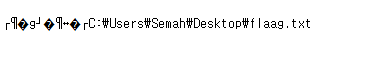

But there is a flag.txt (not flaag.txt) in Desktop/ and it has fake flag.

Likewise, there is only zero size flag.bmp in Documents/my content/ .
So, I used NTFS log tracker to find location where flaag.txt and credentials.txt were moved.


$RVL2F46.txt was flaag.txt

and it's fake flag :) hehe.
Next!


credentials.txt was zipped and renamed to $R002W8L.txt (moved to Recycle.BIN).
credentilas.zip was deleted.

and $R002W8L.txt is zero size in given E01 file.
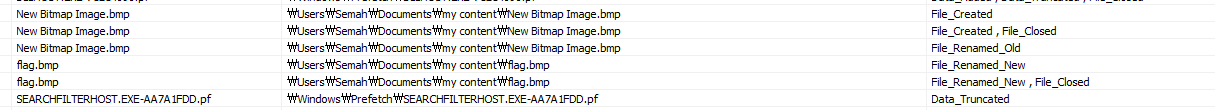
flag.bmp is meaningless.
haha :)

IE history modified log between credentials.txt logs.
IE history :

hmmmmmm..............
--------
[add something after ctf ends.]
왜 저 credentials.zip .txt 를 붙잡고 있었지.. 문제 제목에서도 whatsapp 써먹는거 알 수 있는데..
at first, Investigate chats from WhatsApp messages DB.

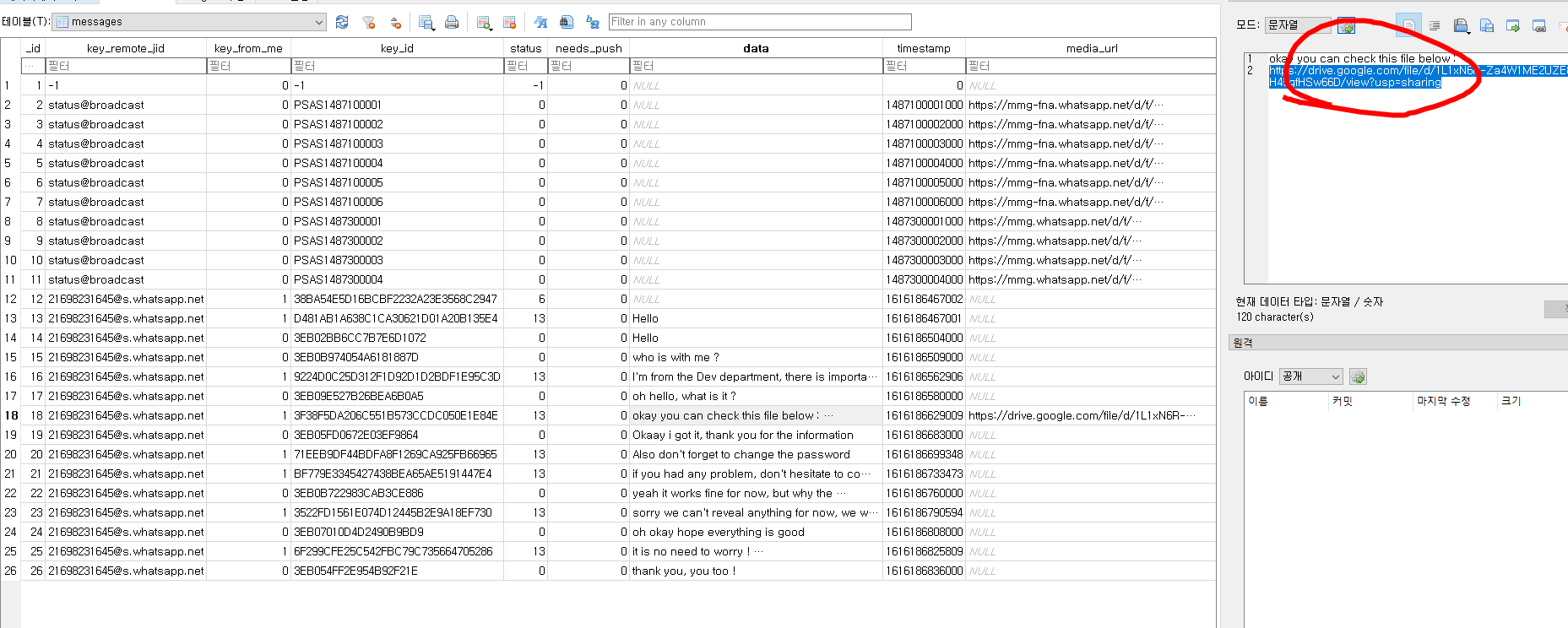
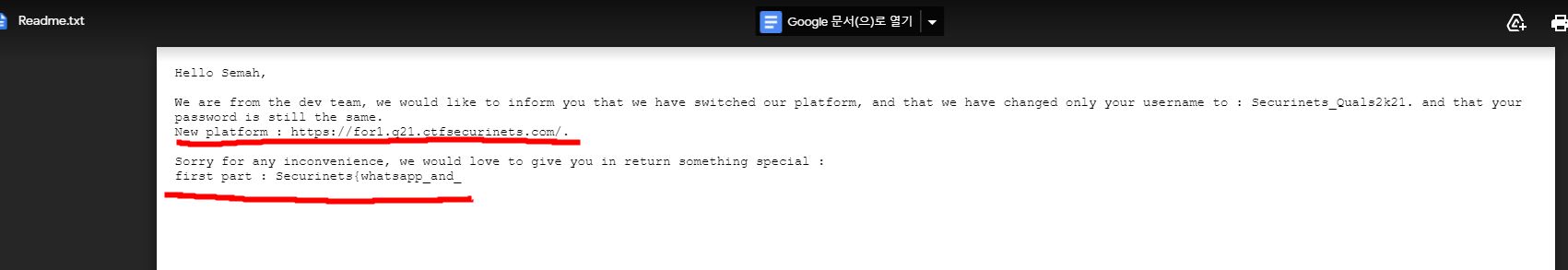
--------
Next! i checked firefox history.


I think flag is in there.
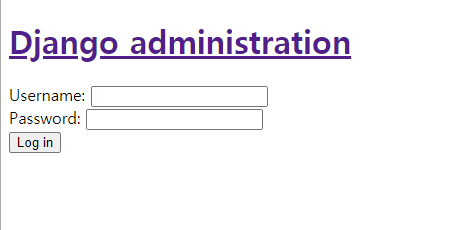
But it need id and pw.

id and pw were stored in logins.json and they were encrypted.
To decrypt them,


create new profile
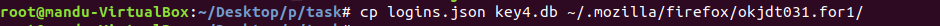
move logins.json and key4.db to new profile folder
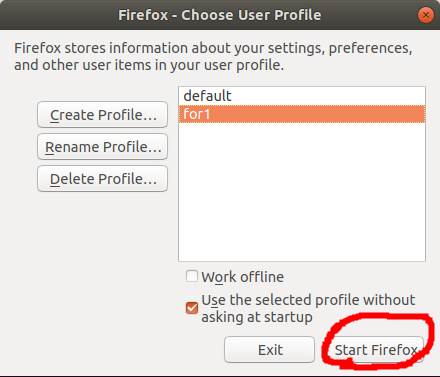
start firefox

yeah!
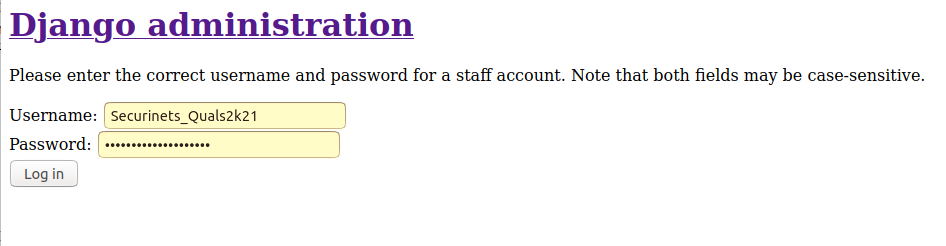
?????????????

oh, another login page is at ./ and i use same account to login.


then i got half of flag.
'CTF Write Up' 카테고리의 다른 글
| RTLxHA CTF 21 write up (0) | 2021.08.01 |
|---|---|
| Securebug.se CTF Loki 2021 write up (0) | 2021.07.19 |
| LINE CTF 2021 write up (0) | 2021.03.21 |
| Codefest CTF 2021 Write up (0) | 2021.03.20 |
| UTCTF 2021 write up (0) | 2021.03.15 |