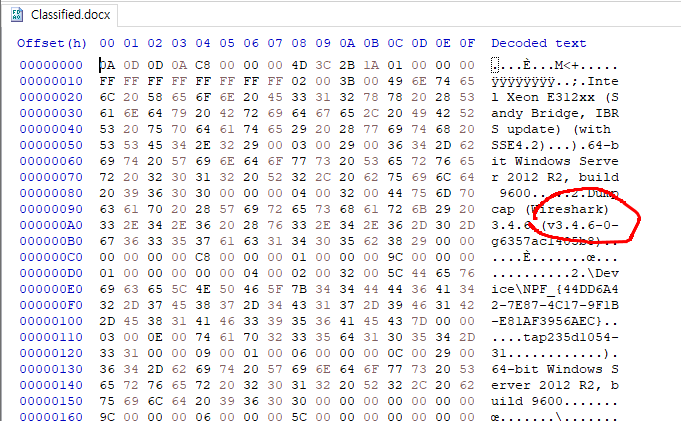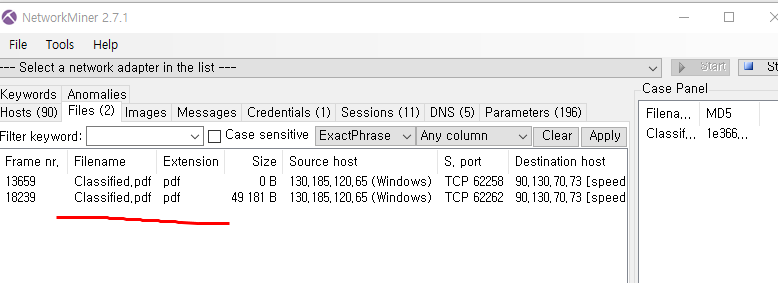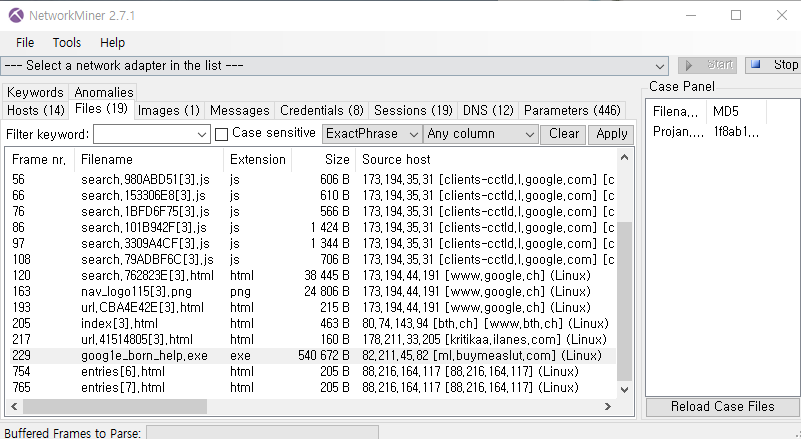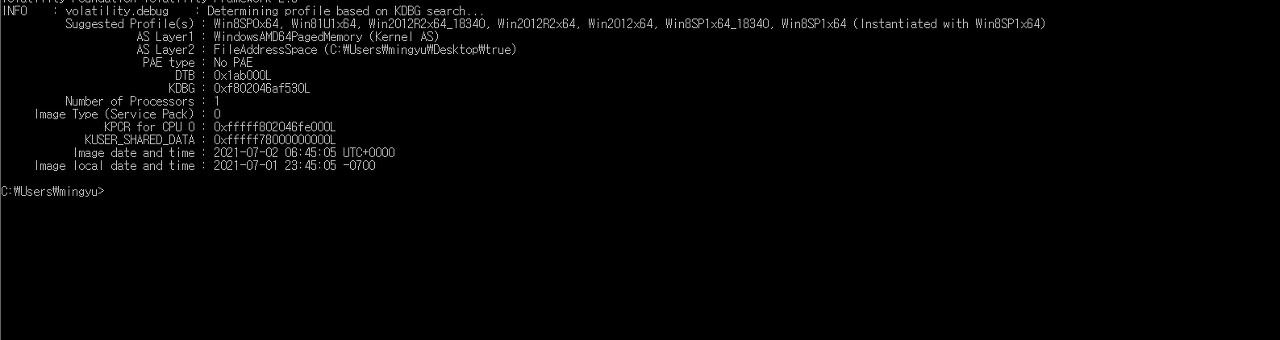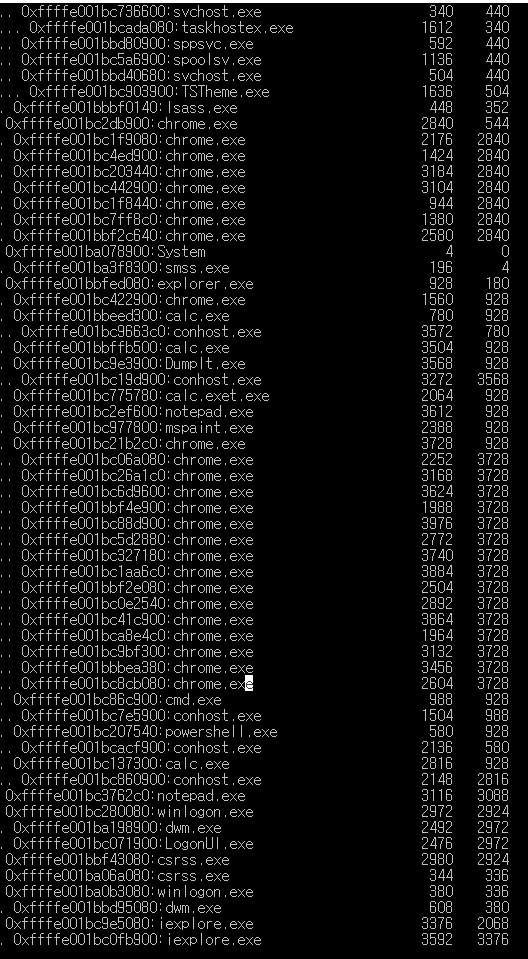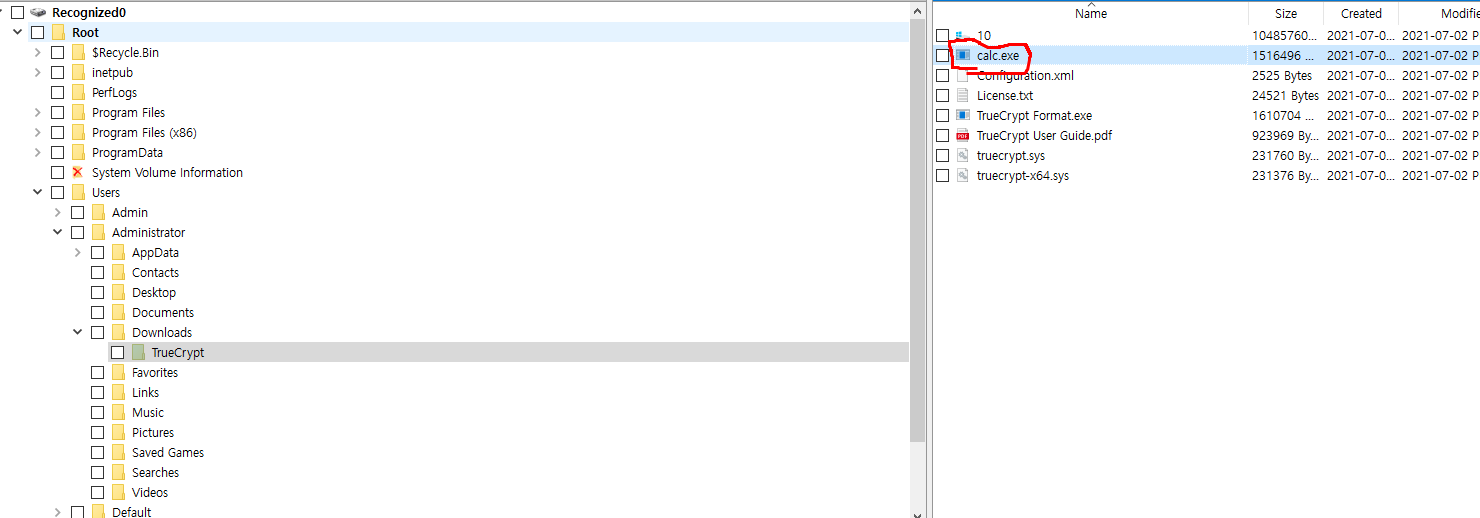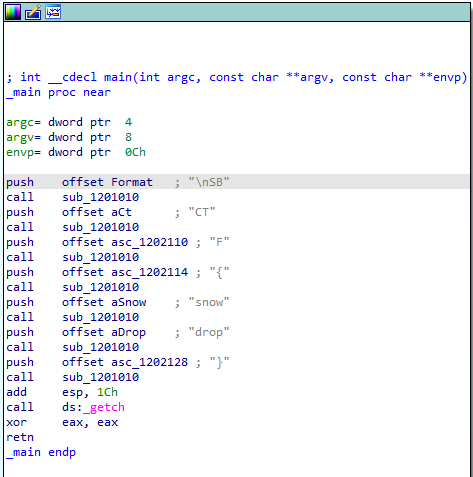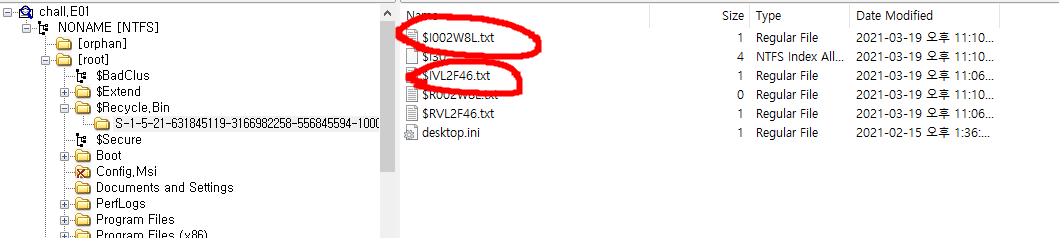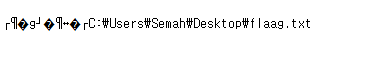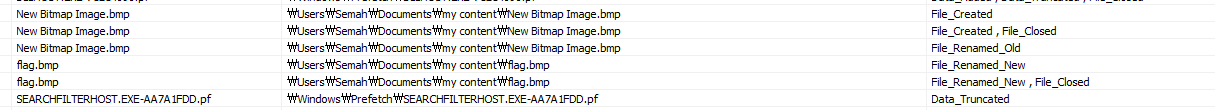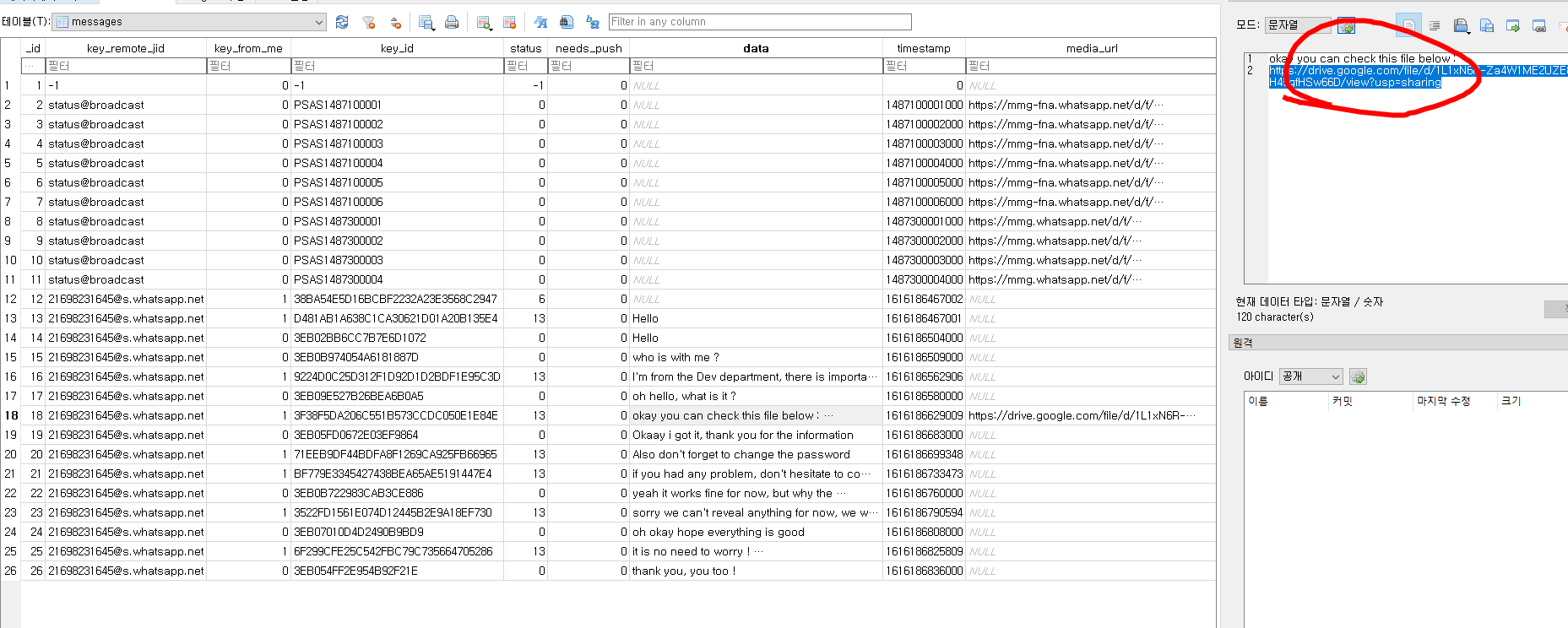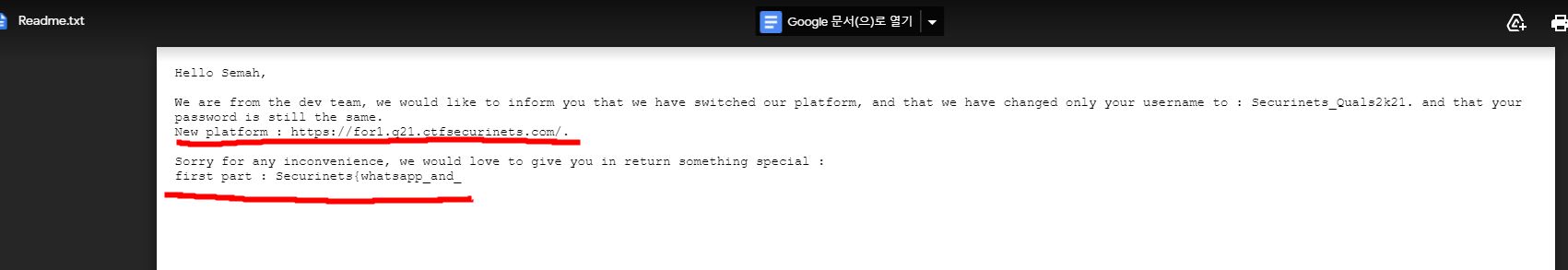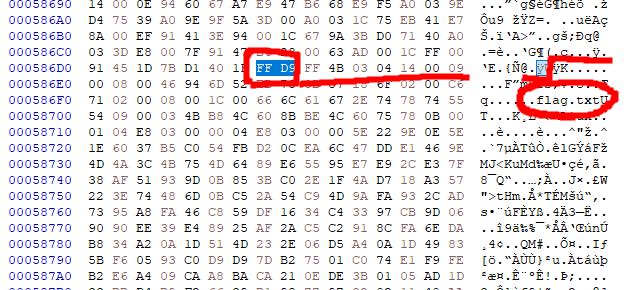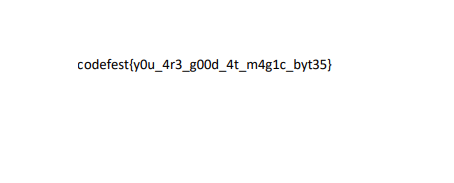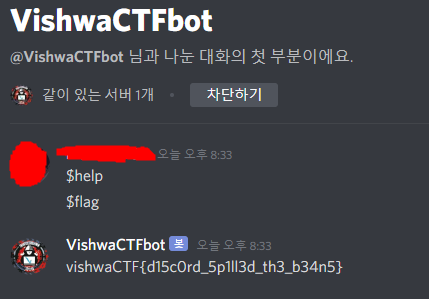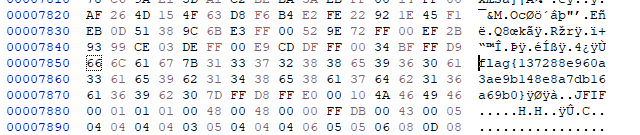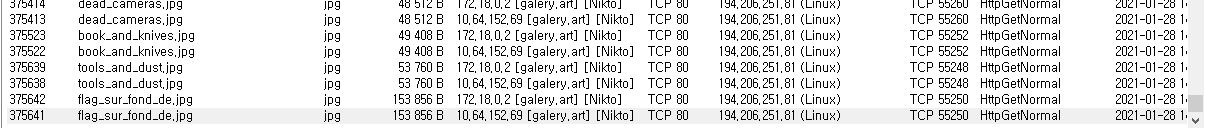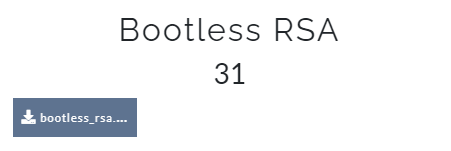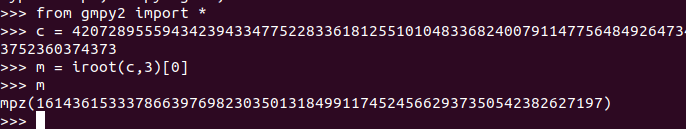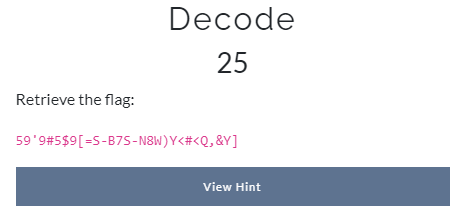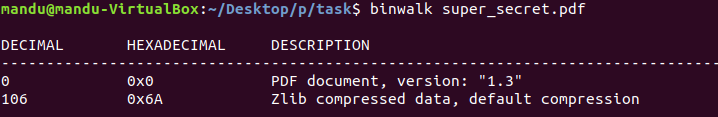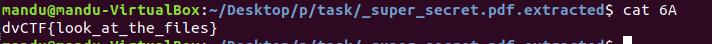
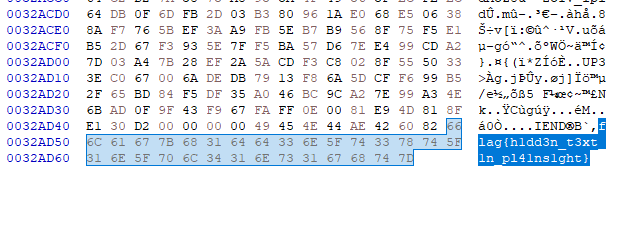

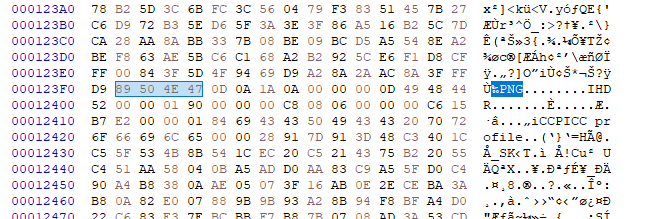
A png file is at the end of jpg file.
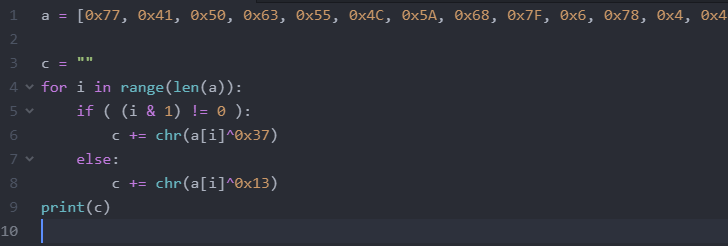
flag{0n3_1m4g3_1s_n0t_3n0ugh}

search "flag{"

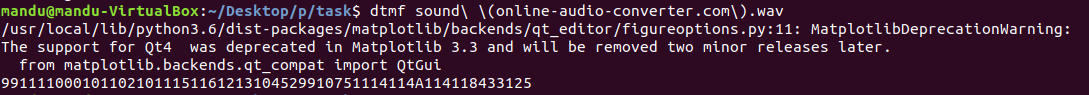
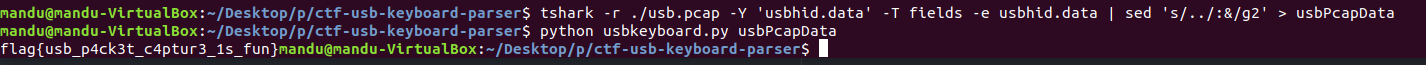
usbhid.data
https://github.com/TeamRocketIst/ctf-usb-keyboard-parser
GitHub - TeamRocketIst/ctf-usb-keyboard-parser: This is the updated script from https://teamrocketist.github.io/2017/08/29/Foren
This is the updated script from https://teamrocketist.github.io/2017/08/29/Forensics-Hackit-2017-USB-ducker/ - GitHub - TeamRocketIst/ctf-usb-keyboard-parser: This is the updated script from https:...
github.com

base64
hex to ascii

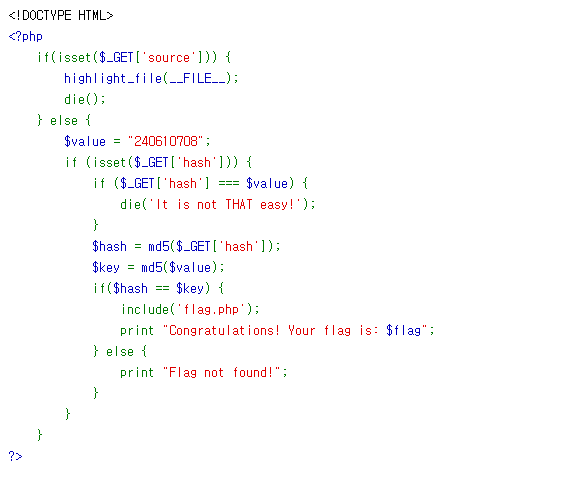
magic hash
?hash=QNKCDZO

change cookie value
base64 encoded
guest -> admin


base64 decode
'CTF Write Up' 카테고리의 다른 글
| SSTF 2021 write up (0) | 2021.08.16 |
|---|---|
| RACTF 2021 Write up (0) | 2021.08.15 |
| RTLxHA CTF 21 write up (0) | 2021.08.01 |
| Securebug.se CTF Loki 2021 write up (0) | 2021.07.19 |
| Securinets CTF Quals 2021 write up (0) | 2021.03.22 |