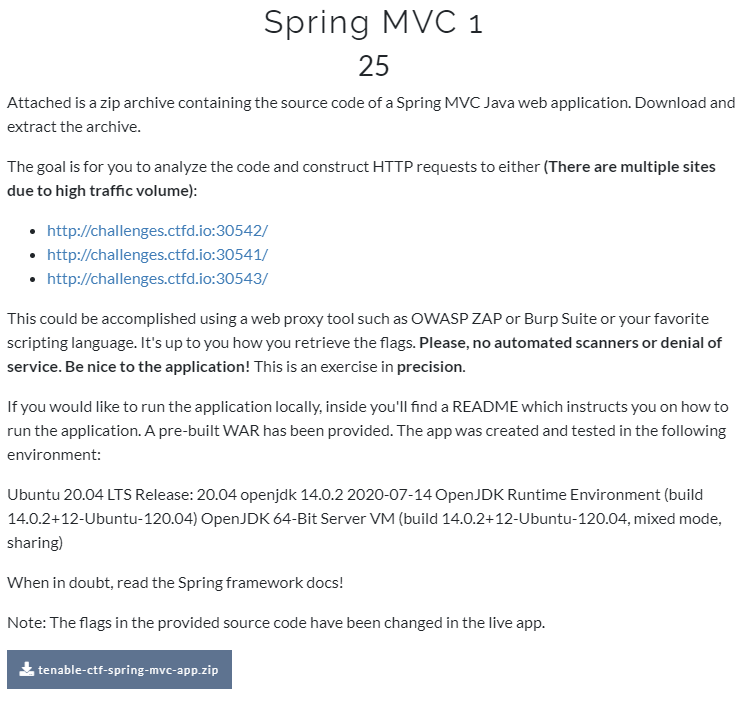
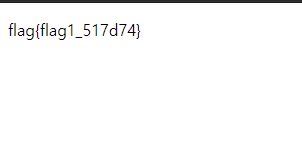
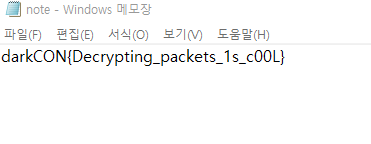
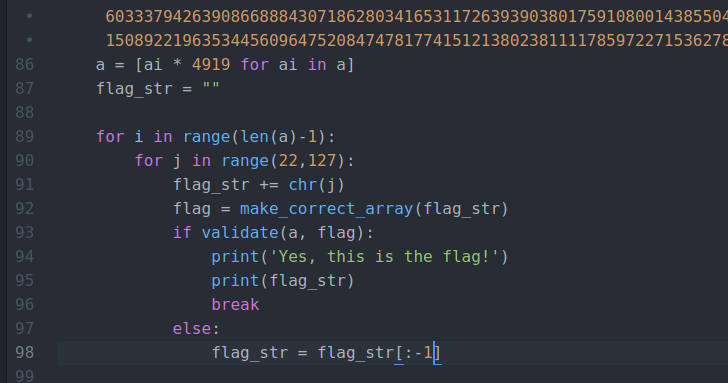
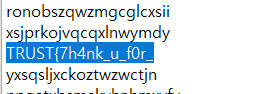blockchain
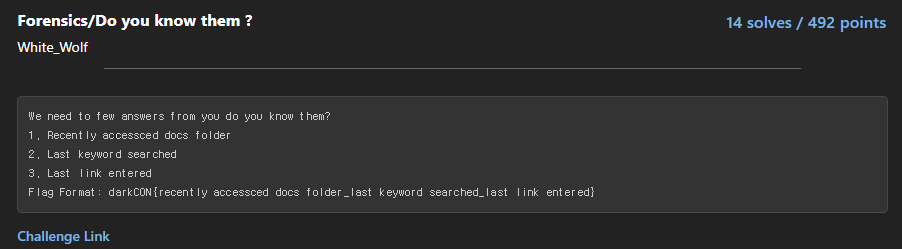
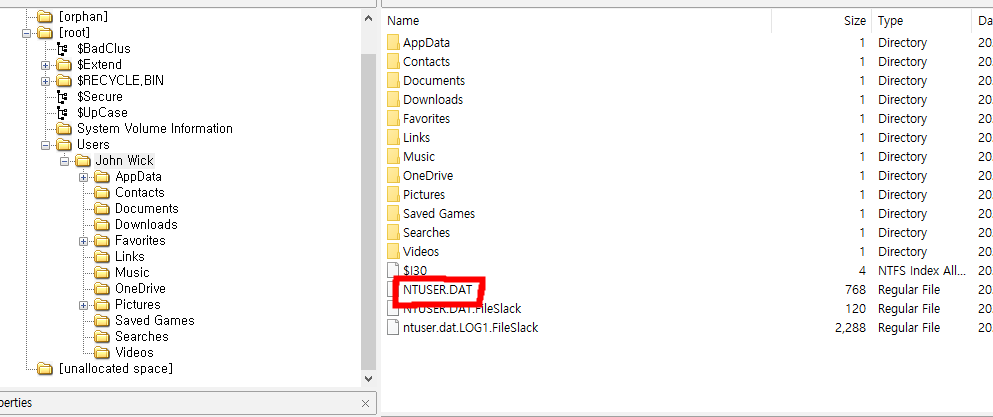
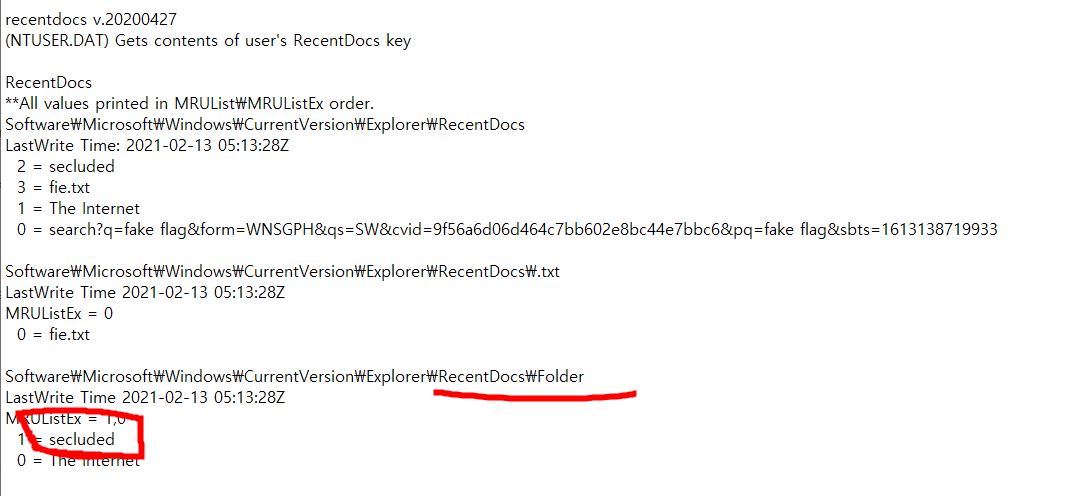
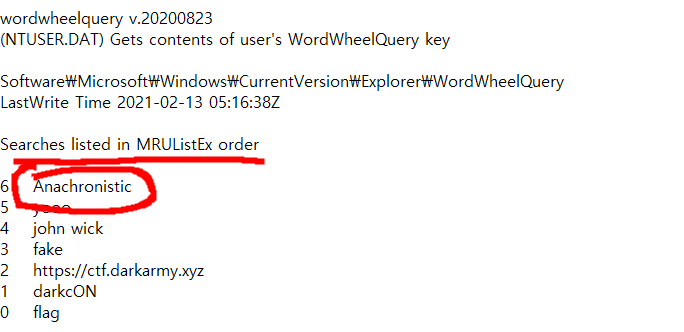
sanity check

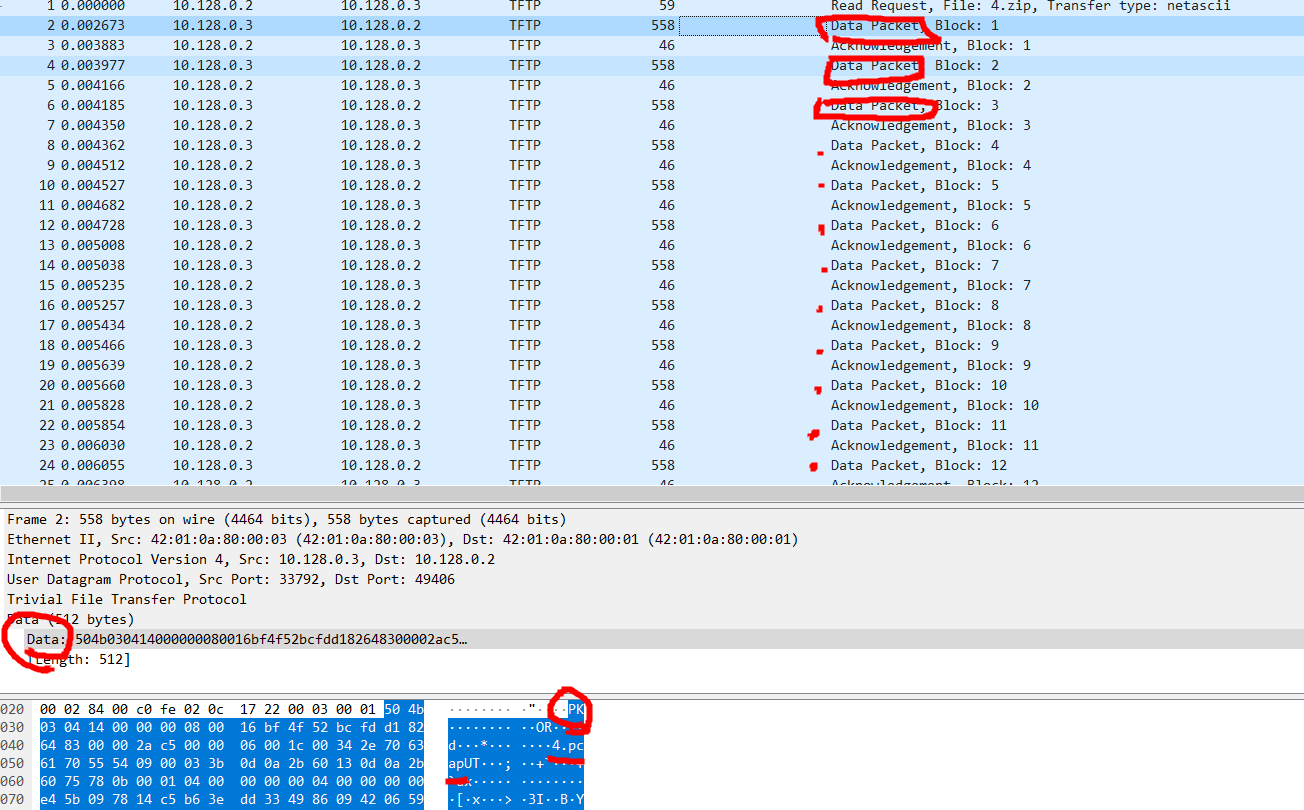
remix.ethereum.org/
Remix - Ethereum IDE
remix.ethereum.org

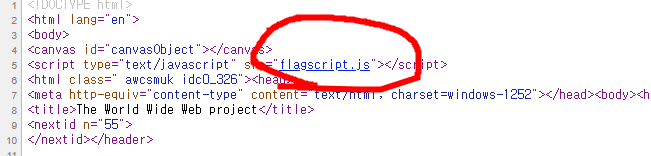
code copy&paste
compile
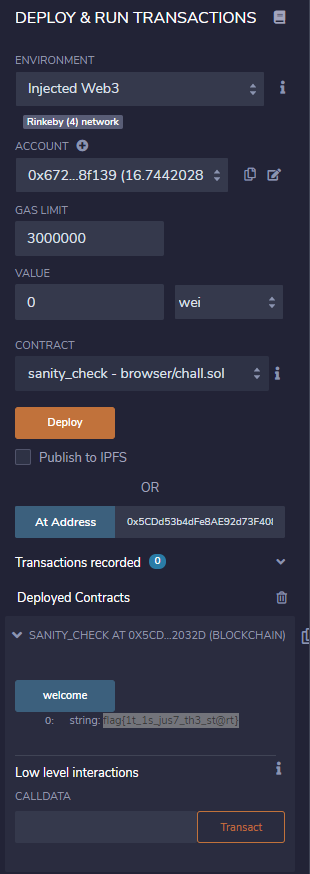
connect metamask rinkeby wallet, load contract address and call welcome func. done.
secure enclave
 0x9B0780E30442df1A00C6de19237a43d4404C5237
0x9B0780E30442df1A00C6de19237a43d4404C5237

It can store text and return text
I thought constroctor of this contract store the flag in this contract.
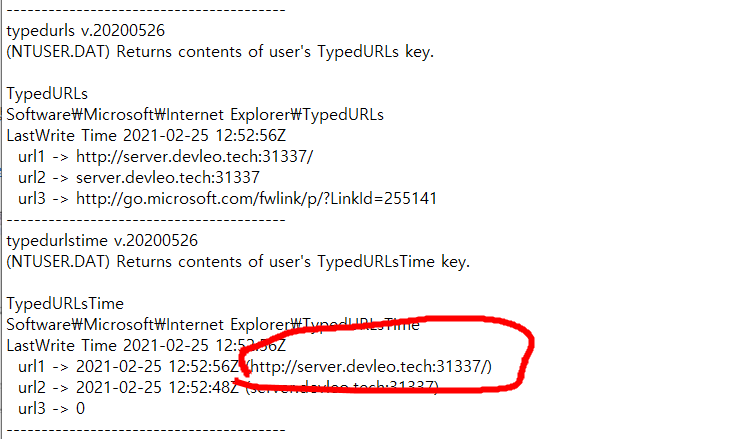
When you call set_secret to store some string, transaction occurs.
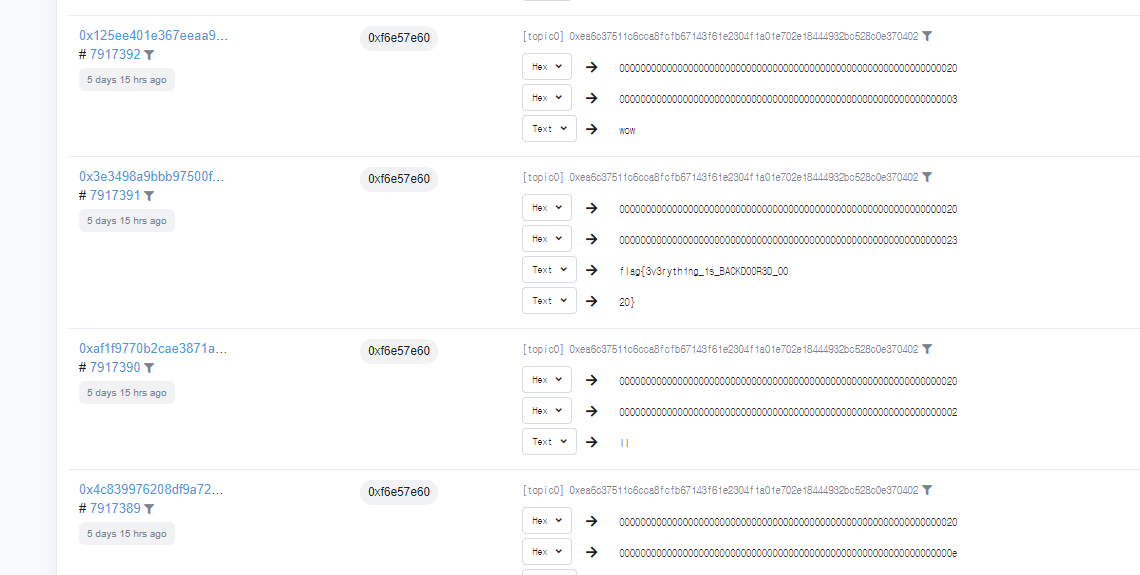
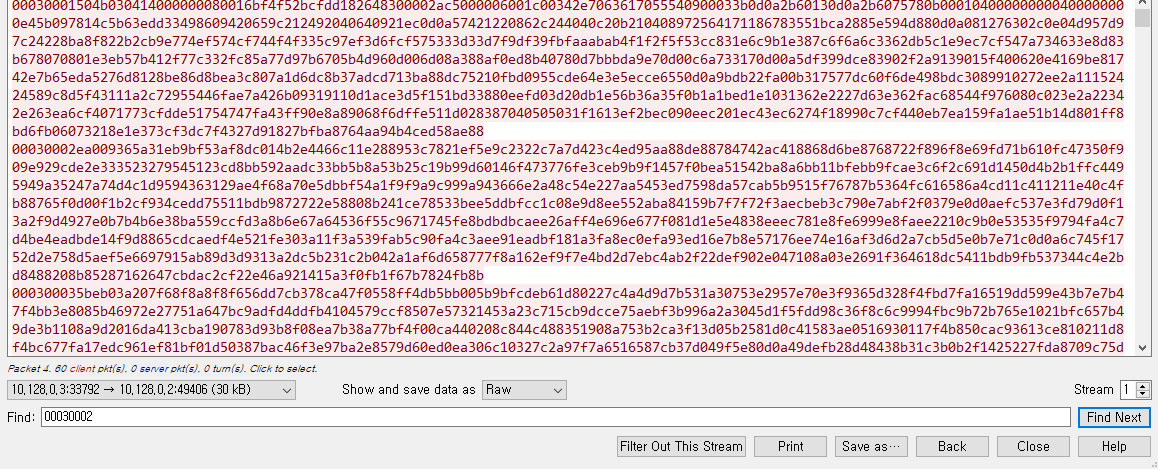
I could find a transaction at etherscan
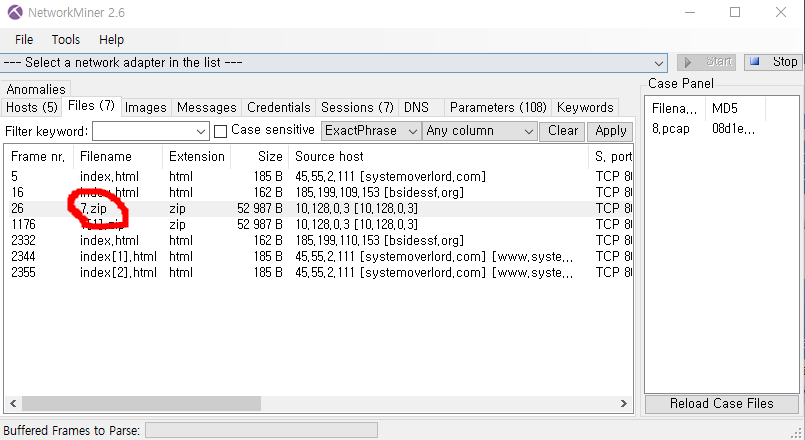
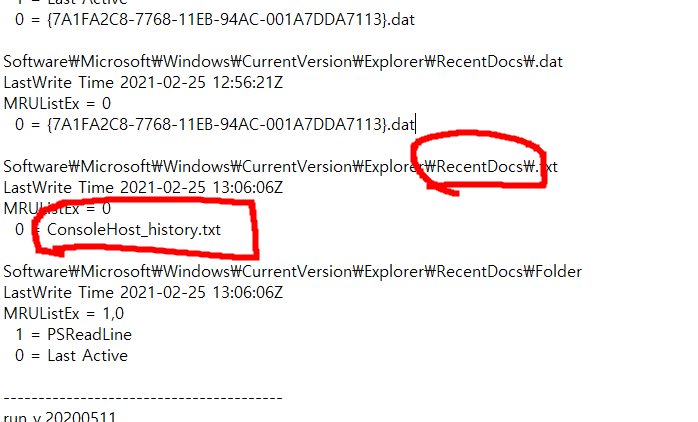
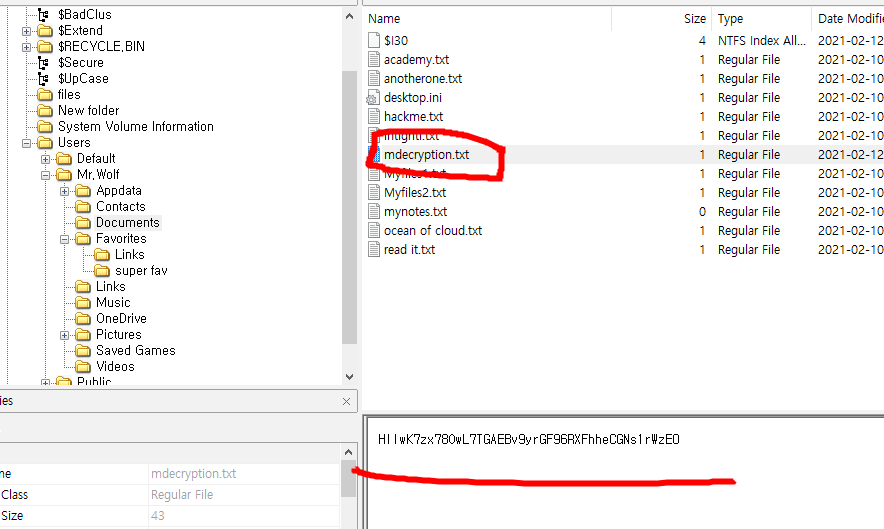
crackme.sol
 0xDb2F21c03Efb692b65feE7c4B5D7614531DC45BE
0xDb2F21c03Efb692b65feE7c4B5D7614531DC45BE

"arg3 is a overflow" is a hint in line 6.
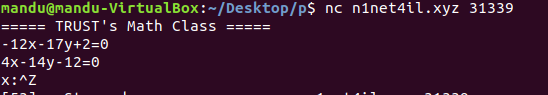
uint MaxValue + 1 = 0
so, i can pass line 7 and 11 condition.
uint is short for uint256, so maximum value is 2**256-1
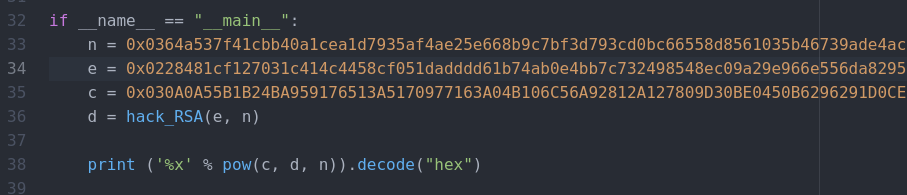
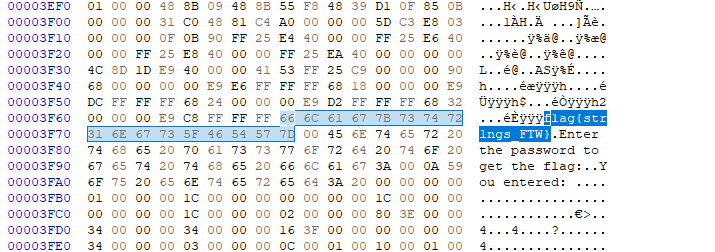
arg3 = 115792089237316195423570985008687907853269984665640564039457584007913129639935
arg1 = 20 ^ 0x70 = 100
decrypt(arg2) = "offshift ftw"
ah just brute force a-z :)
arg2 = evvixyvj vjm
"100","evvixyvj vjm","115792089237316195423570985008687907853269984665640564039457584007913129639935"

compile error

To find correct uint array size, brute force all value.
if size is over 26 :

if size is equal 26:
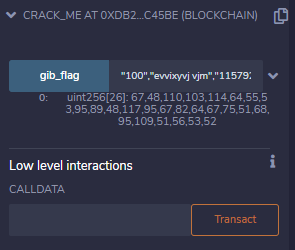
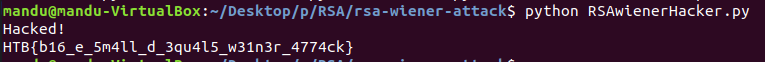
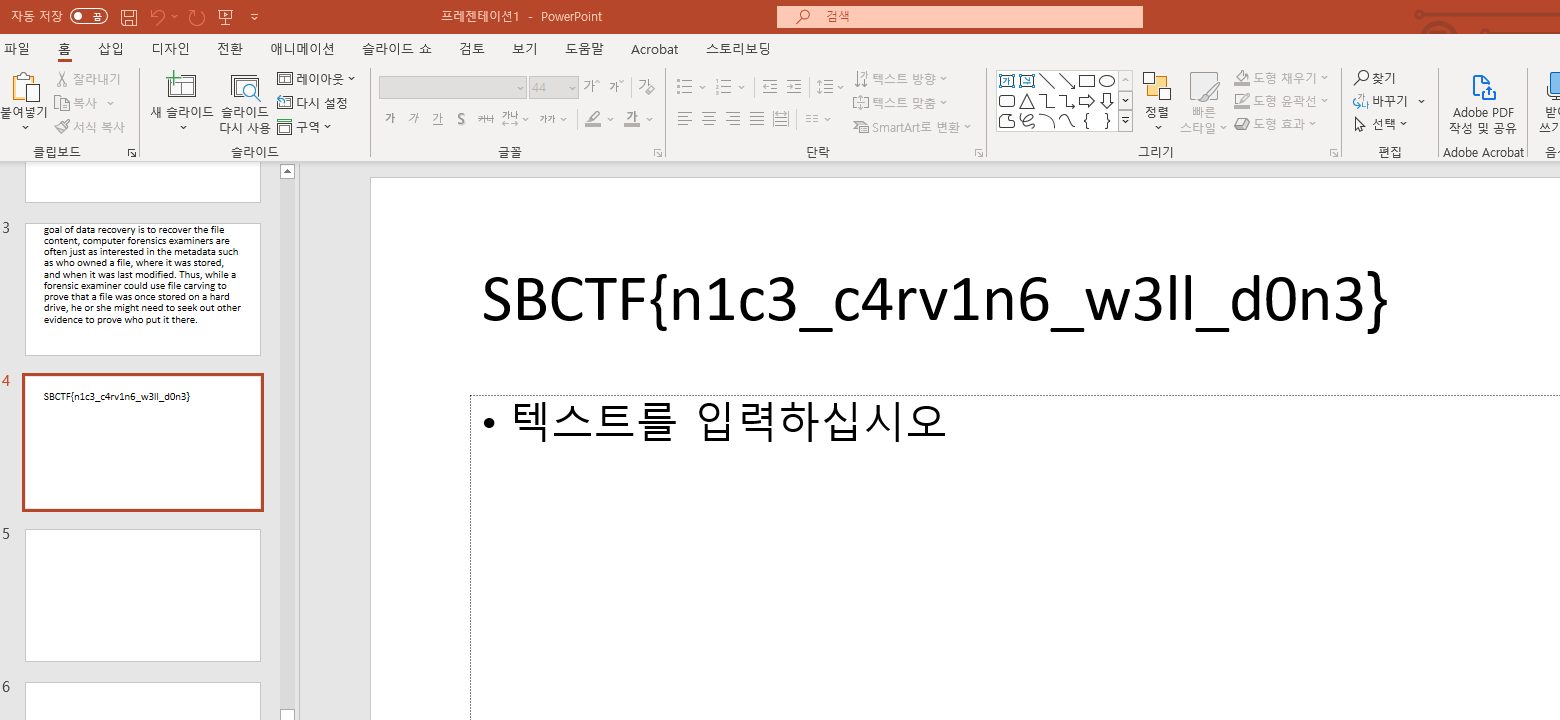
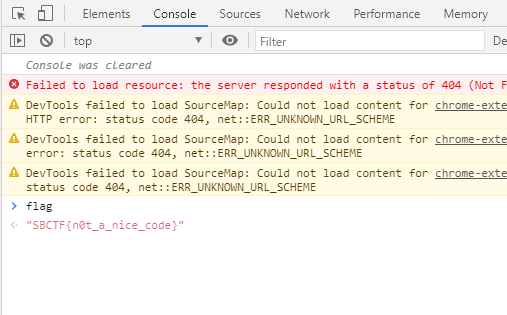
got a flag.
crypto casino
 0x186d5d064545f6211dD1B5286aB2Bc755dfF2F59
0x186d5d064545f6211dD1B5286aB2Bc755dfF2F59
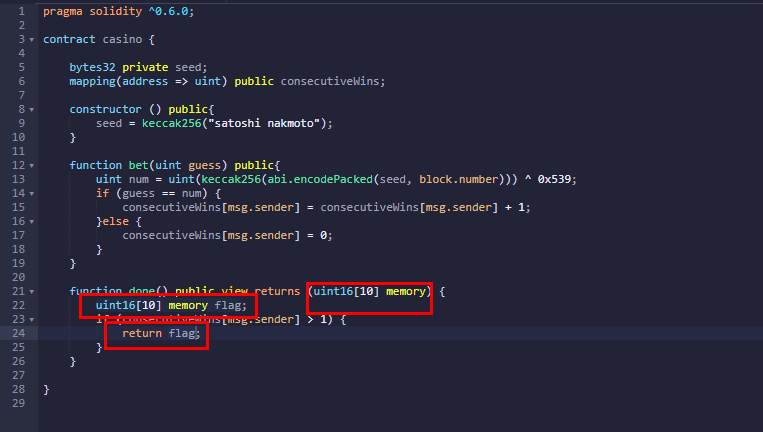
Edit code to get ouput value correctly.
To get a flag, need guessing and correct two times.
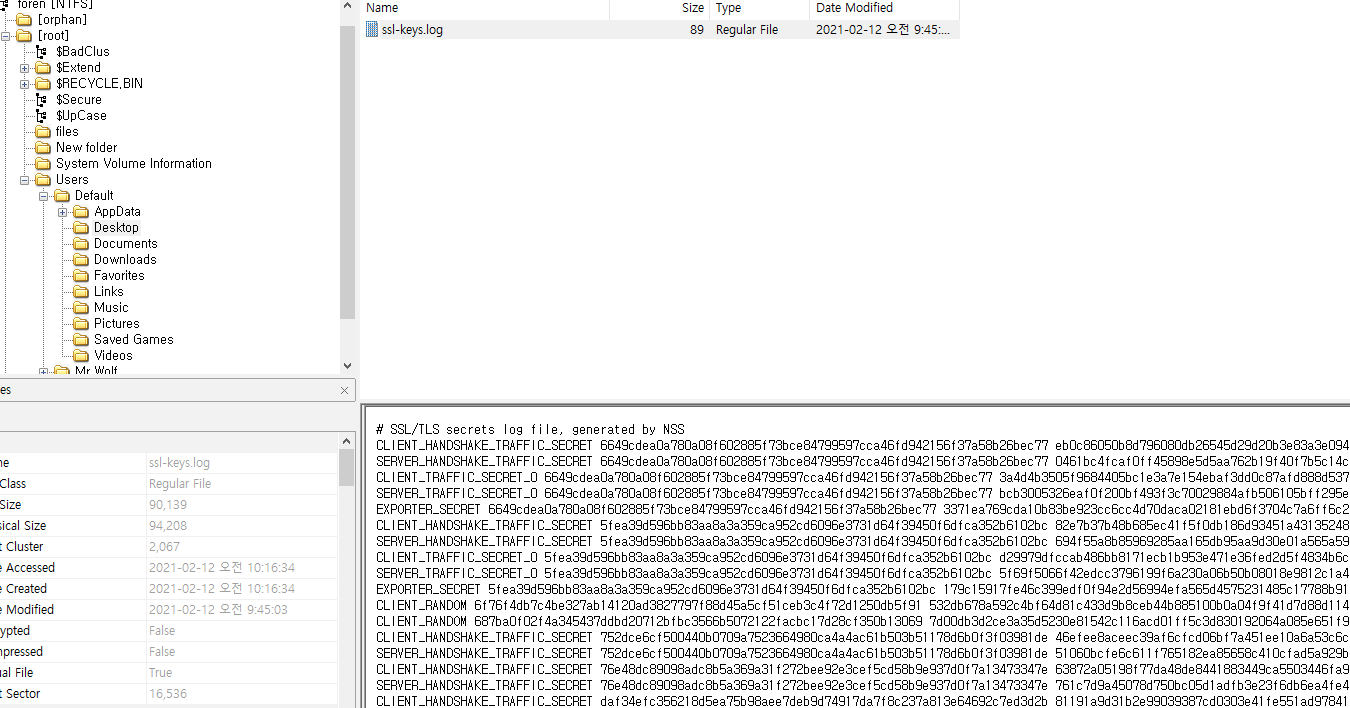
seed = b37c910f4e0df0efafb35a55489604369808b6de642ff1dbab5062680afaddcd

the block.number is the number of the mined block containing the transaction.

deploy a contract that returning result of uint(keccak256(abi.encodePacked(seed, block.number+3))) ^ 0x539
get block.number and hash
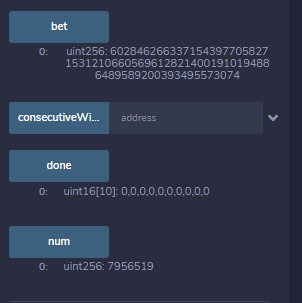
hash <= block.number <= 7956519 + 3
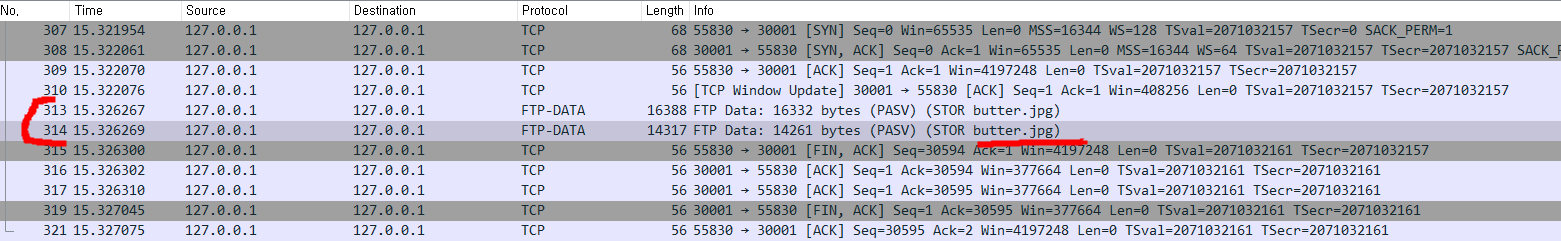
Then pend transaction that call bet(60284626633715439770582715312106605696128214001910194886489589200393495573074) before #7956522 block mined.

hmm out of gas

increase gas price and gas limit.
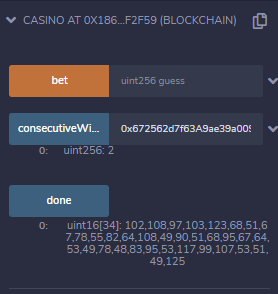
done.
RICH CLUB
 0xC7bEc01281648D3A7F9BB86B811A2de5B1E0cc61
0xC7bEc01281648D3A7F9BB86B811A2de5B1E0cc61

hmm
for line 21, swap eth to uniswap app.uniswap.org/#/swap
Uniswap Interface
app.uniswap.org
 600 -> 601
600 -> 601
hmm
grant_membership() function에 pubkey를 넘겨주면 encoded flag를 넘겨준다고 한다.
그럼 그걸 decrypt 하면 된다고 하는데
그럼 solidity 코드는 어떻게 수정해서 써먹어야되는거야 :(
crypto
factorize

p와 q의 상위 512비트는 base로 동일함.
따라서 sqrt(n)의 상위 512비트와 동일.
hmm
엥 그냥 factorize 돌리면 됐었던 문제였넹
optimizer

별거 없다. simple.
주어진 배열 정렬할 때 이동 횟수 구해서 입력해주면 된다.

pyjail

hmm
0x414141

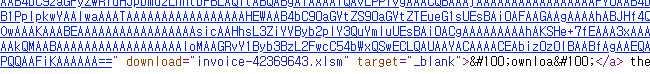
go to www.offshift.io/
You are being redirected...
www.offshift.io

go to github
github.com/offshift-dev
offshift-dev - Overview
Cryptographically private offshore storage & DeFi protocol on Ethereum - offshift-dev
github.com

There are two commits in january 2021

interesting

click

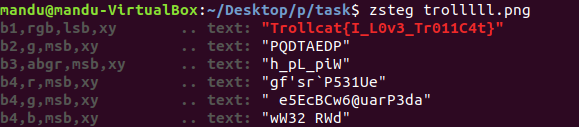
download pyc file.

decompile pyc using uncompyle6
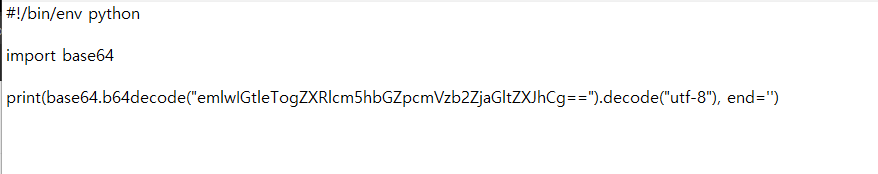
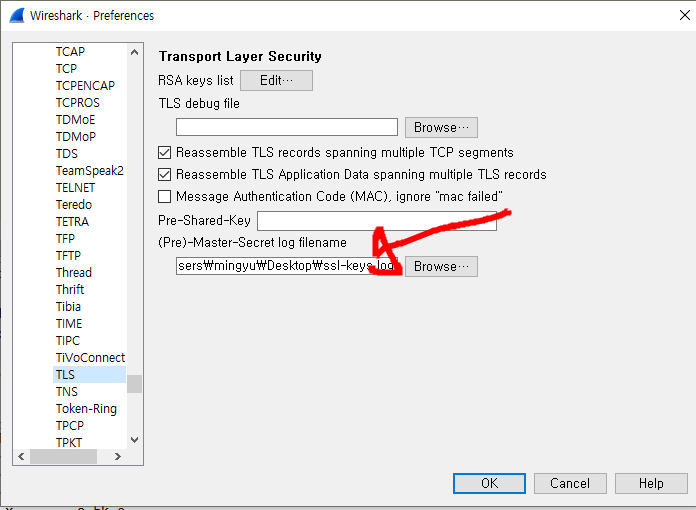
decrypt

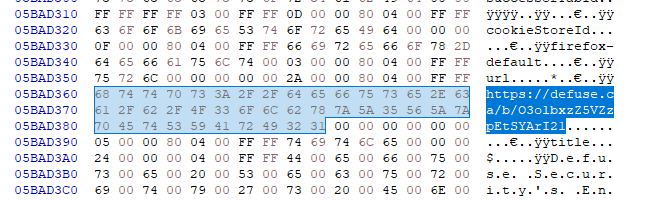
a link!

download a smashing.pdf via mega link.

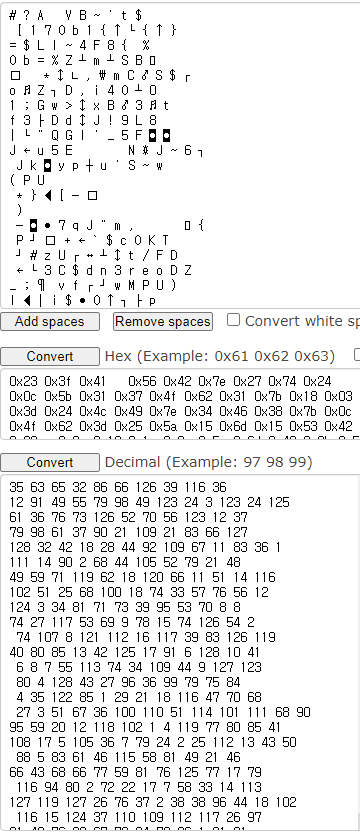
hmm is it xor?

correct!

bitcoin paper..?

compare with smashing.pdf and original bitcoin paper pdf.
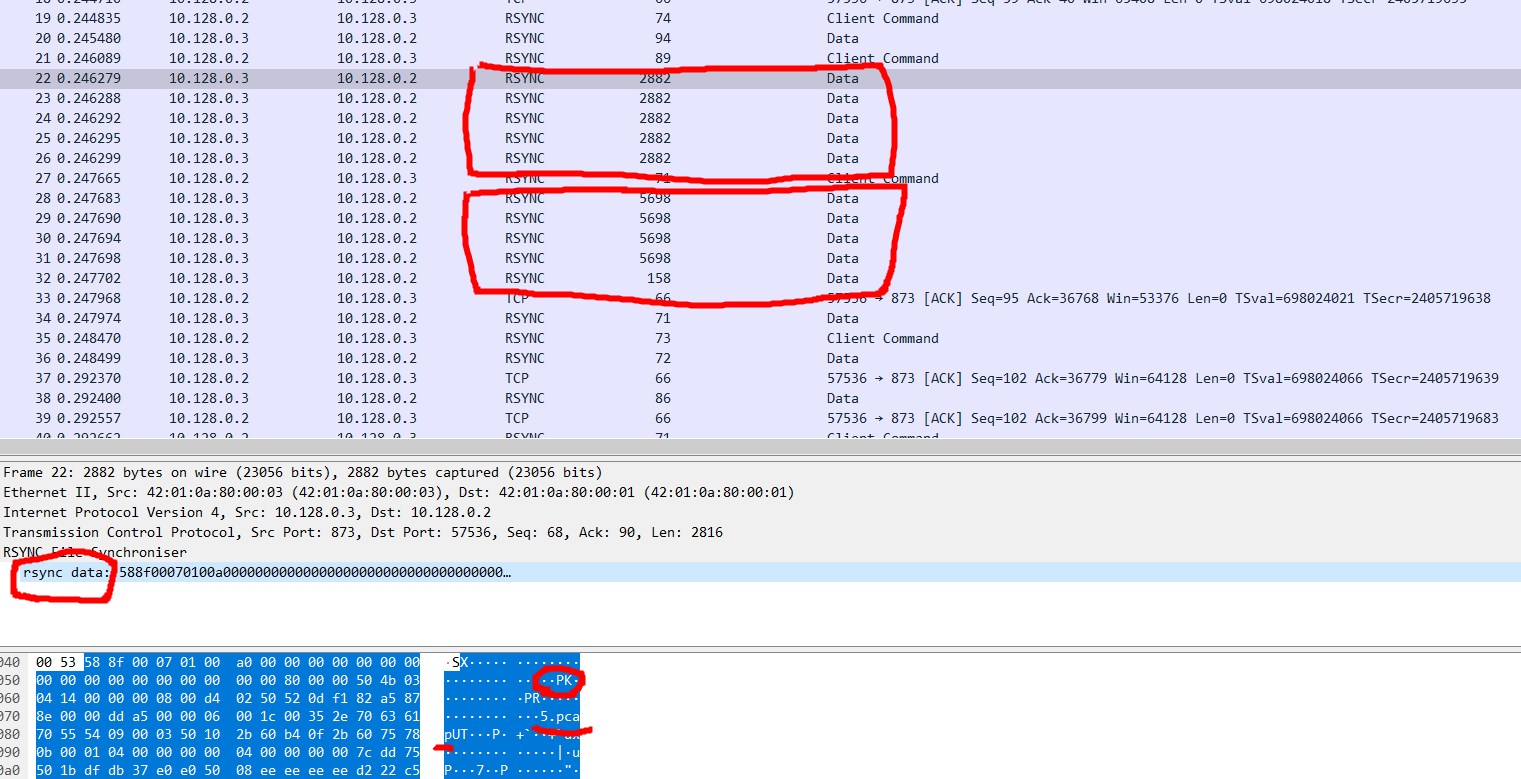
smashing.pdf is a little bigger.

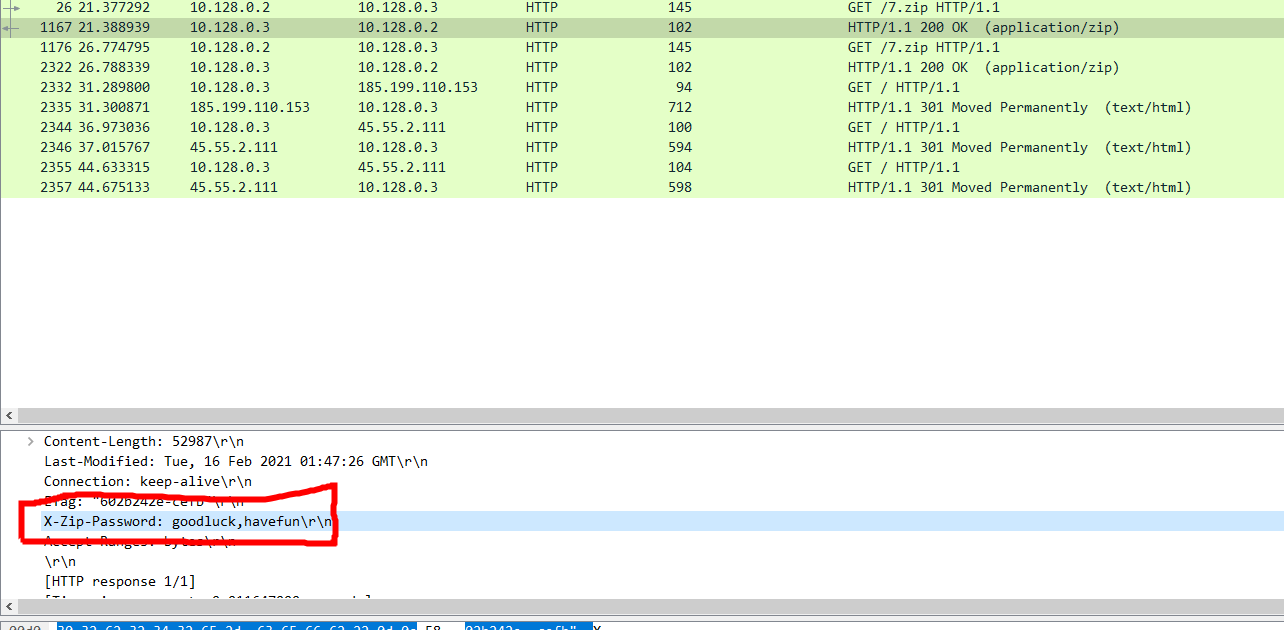
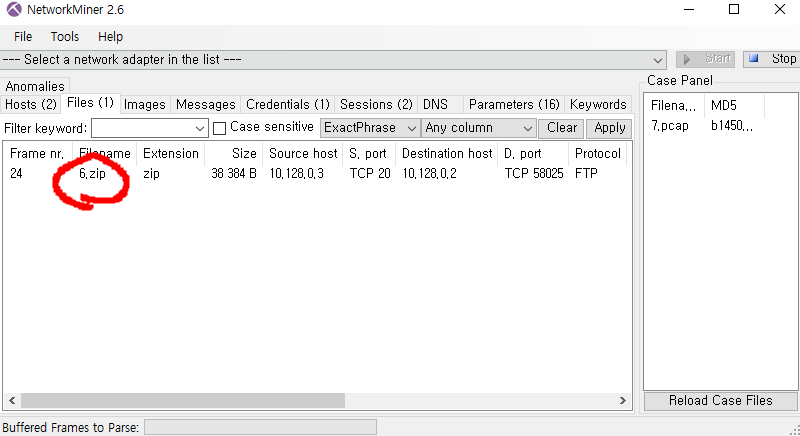
a zip file is here :)
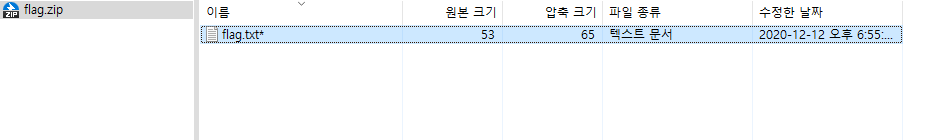
is locked.
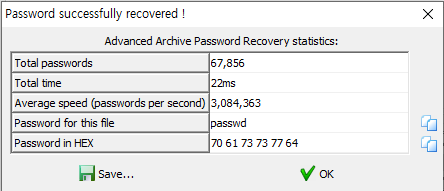
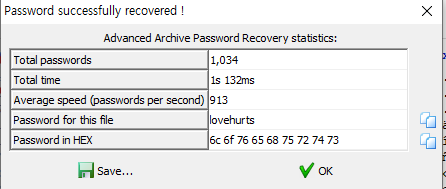
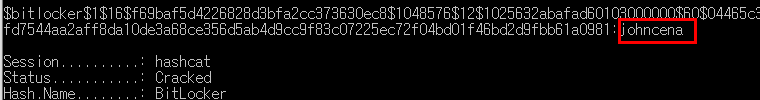
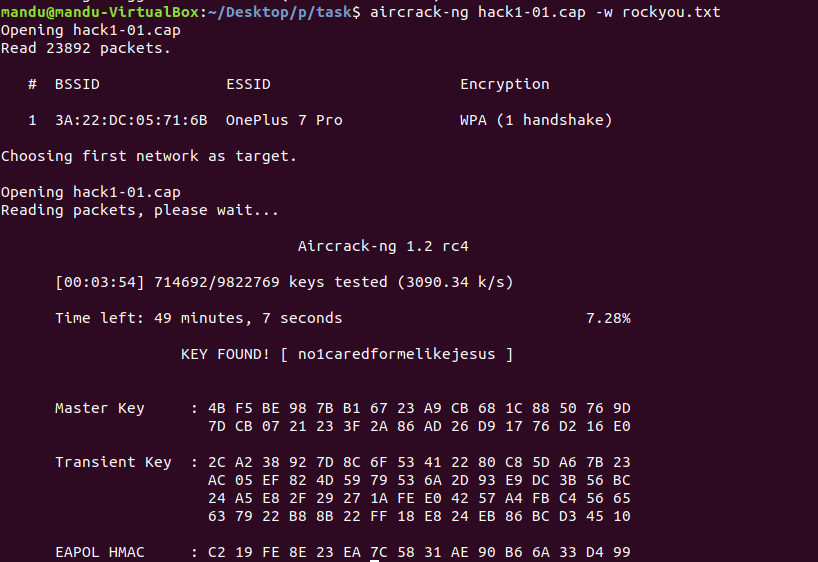
dictionary attack
dictionary file i used : rockyou.txt
 i got it
i got it
file reader
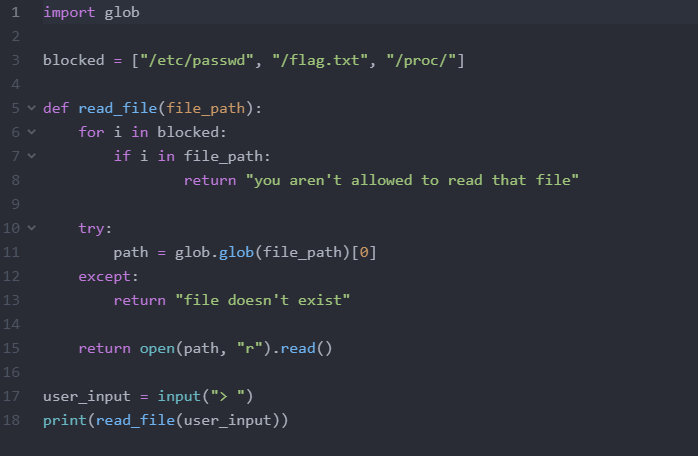
it filters "/flag.txt"
but we can get all .txt files using glob.glob("*.txt").

Shjail

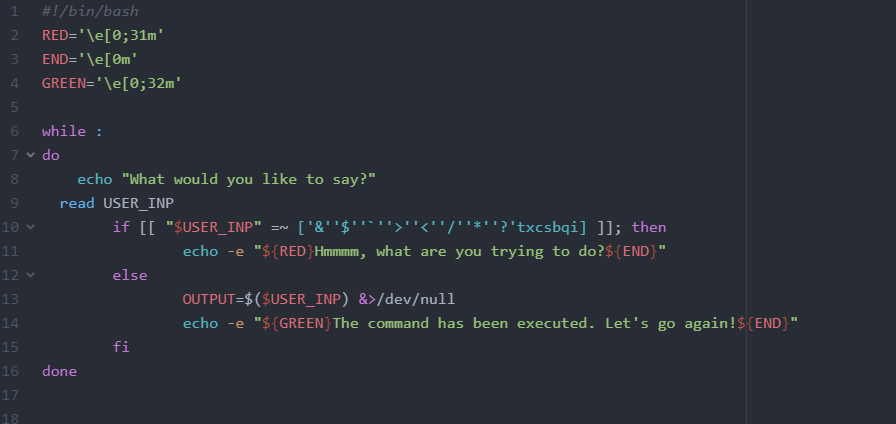
eval eval py{r..u}hon\\ -m\\ S{h..j}mpleHTTPServer\\;

hmm
perl flag.[a-z][a-z][a-z]
web
graphed 2.0

there is a input form

There is a code send graphql query.

gist.github.com/craigbeck/b90915d49fda19d5b2b17ead14dcd6da
Introspection query for GraphQL
Introspection query for GraphQL. GitHub Gist: instantly share code, notes, and snippets.
gist.github.com
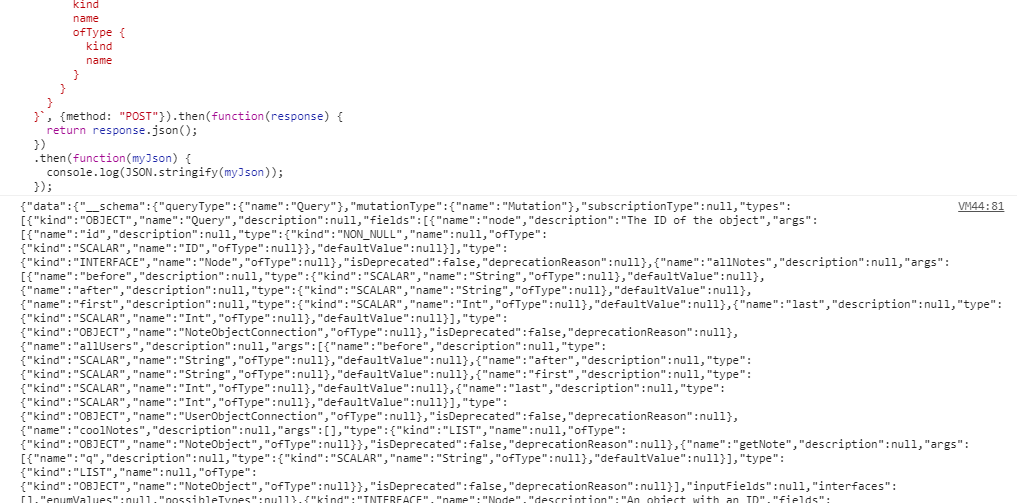

i found a fake flag :(

no flag in users

no flag in coolnotes
hmm
아 역시 getNote를 사용하는 것이었다.
하나 남은게 getNote였는데, q에 뭐가 들어가는지 몰라서 포기했는데..
쿼리문을 넣어버리는 거였넹.
maze


./robots.txt
 ./robots.txt
./robots.txt
./sup3r_secr37_@p1

good.

hmm
아 username이 pop_eax가 아니라 XFT였다.
hackme
?cmd=help

?cmd=123456

hmm
nl /*
nl *
>cat
* /f*