Team : N0Named
제가 푼 문제만 풀이를 적었습니다.
Misc
Strong Password
Eat, Drink, Pet, Hug, Repeat!
flags are entered in the format rtcp{flag}
Hints
-
Words are separated by underscores ("_")
-
Come on, repeat it! Just once!
먹는거 마시는거 애완동물 안아주기
반복!
밥 차 고양이 판다
flag : rtcp{rice_tea_cat_panda}
Forensics
Allergic College Application
100
I was writing my common app essay in Mandarin when my cat got on my lap and sneezed. Being allergic, I sneezed with him, and when I blew my nose into a tissue, the text for my essay turned really weird! Get out, Bad Kitty!
hxd로 파일 열어서 hex값 복사해다가 아래 사이트에서 인코딩을 변경해주었다.
https://dencode.com/string/hex
Hexadecimal String Converter Online - DenCode
Hexadecimal String Converter. (e.g. "Hello, world!" <=> "48 65 6C 6C 6F 2C 20 77 6F 72 6C 64 21")
dencode.com
GB18030 이나 EUC-CN 인코딩을 사용할 경우 다른 글자 깨짐 없이 전부 한자로 깔금하게 나온다.
설마하고 구글번역 돌려보니.. 깔끔한 문장이었다.
flag : {我_只_修改_了_两_次}
cat-chat
125
nyameowmeow nyameow nyanya meow purr nyameowmeow nyameow nyanya meow purr nyameowmeow nyanyanyanya nyameow meow purr meow nyanyanyanya nya purr nyanyanyanya nya meownyameownya meownyameow purr nyanya nyanyanya purr meowmeownya meowmeowmeow nyanya meownya meowmeownya purr meowmeowmeow meownya purr nyanyanyanya nya nyameownya nya !!!!
냐 냐냐냐냐냐프르르르르르
사용된 단어는 3가지이다.
In that conversation, 3 word used: nya, meow, purr
it seems like morse code.
nya => .
meow => _
purr => /
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
MORSE_CODE_DICT = { 'A':'._', 'B':'_...',
'C':'_._.', 'D':'_..', 'E':'.',
'F':'.._.', 'G':'__.', 'H':'....',
'I':'..', 'J':'.___', 'K':'_._',
'L':'._..', 'M':'__', 'N':'_.',
'O':'___', 'P':'.__.', 'Q':'__._',
'R':'._.', 'S':'...', 'T':'_',
'U':'.._', 'V':'..._', 'W':'.__',
'X':'_.._', 'Y':'_.__', 'Z':'__..',
'1':'.____', '2':'..___', '3':'...__',
'4':'...._', '5':'.....', '6':'_....',
'7':'__...', '8':'___..', '9':'____.',
'0':'_____', ', ':'__..__', '.':'._._._',
'?':'..__..', '/':'_.._.', '_':'_...._', '_':'..__._',
'(':'_.__.', ')':'_.__._', ' ':'/', '\n':'\n', '':'', ':':"___...", '\'':'.____.'}
def decrypt(message):
message += ' '
message = message.replace("nya",".")
message = message.replace("meow","_")
message = message.replace("purr","/")
decipher = ''
citext = ''
for letter in message:
if (letter != ' ' and letter != '\n'):
i = 0
citext += letter
else:
i += 1
if i == 2 :
decipher += ' '
else:
decipher += list(MORSE_CODE_DICT.keys())[list(MORSE_CODE_DICT.values()).index(citext)]
citext = ''
return decipher
def main():
message = '''nyameowmeow nyameow nyanya meow purr nyameowmeow nyameow nyanya meow purr nyameowmeow nyanyanyanya nyameow meow purr meow nyanyanyanya nya purr nyanyanyanya nya meownyameownya meownyameow purr nyanya nyanyanya purr meowmeownya meowmeowmeow nyanya meownya meowmeownya purr meowmeowmeow meownya purr nyanyanyanya nya nyameownya nya'''
result = decrypt(message)
print(result)
if __name__ == '__main__':
main()
|
cs |
WAIT WAIT WHAT THE HECK IS GOING ON HERE
good
than, go to the discord channel and copy all of the cat-chat and decode it!
than you can find this:
RTCP:TH15_1Z_A_C4T_CH4T_N0T_A_M3M3_CH4T
flag : RTCP{TH15_1Z_A_C4T_CH4T_N0T_A_M3M3_CH4T}
Chugalug's Footpads
Chugalug makes footpads that he can chug and lug. However, his left one is different from his right... I wonder why?
I downloaded 2 files: left.jpg and right.jpg
They seems that they are perfectly same, but they are not.
I used cmp command to find different data between left.jpg and right.jpg.
$ cmp -l right.jpg left.jpg
1720 122 162
1721 115 164
2041 105 143
2042 121 160
2328 160 173
2329 165 124
2330 102 150
2854 240 63
2855 63 172
2856 154 145
3016 144 137
3017 201 136
3019 24 162
3110 161 63
3332 14 137
3626 21 156
3627 232 60
4215 112 124
4405 40 143
4413 2 110
4775 62 64
4776 347 156
5125 57 103
5149 114 61
5150 112 141
5400 364 65
5401 362 175
|
1
2
3
4
5
6
7
|
c = [162,164,143,160,173,124,150,63,172,145,137,136,162,63,137,156,60,124,143,110,64,156,103,61,141,65,175]
flag = ""
for cc in c:
flag += chr(int(str(cc), 8))
print flag
|
cs |
flag : rtcp{Th3ze_^r3_n0TcH4nC1a5}
Motivational Message
My friend sent me this motivational message because the CTF organizers made this competition too hard, but there's nothing in the message but a complete mess. I think the CTF organizers tampered with it to make it seem like my friend doesn't believe in me anymore, but it's working like reverse psychology on me!!!!
motivation!!!!!.txt 파일 하나가 주어진다.

It's reversed PNG file!
reverse it!
< motivation.txt xxd -p -c1 | tac | xxd -p -r > file.png
But there is no flag in picture.
I used zsteg and i can find a flag!
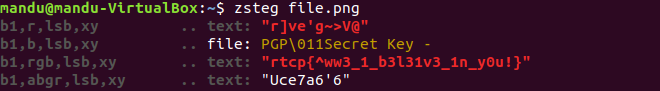
Web
growls at the chicken
grrrrrrR
big chicken, i hisS At you!!!
Hints
NQr2MIa1jsaifAVOn3zYeMynNJwd4oBiiem4fJHsA1WjzfyhUp1+seCW0GMijoDHb3w9BMKj7aw6hhtae5/Qw5xOqMioJU3vvEj0BEHO1wInPqlOeTRdZb8BcTsXP+Z/KBA2FjSZcpGHo7rOZ7NtR15y3eY4s/e/tgKUHvPe9MdmDe1kINtyRXgjghJO9e3uMEQmFe2Ai5moVnG7yIVfUd3QG6/Z+K4PSttbJtjWSLFO7zpmYpEOg3XBxsOw/w5scJQqJ7OLGiH22u4+JFXRlD/wPmDzk9uYlLWLcCuxnY0xuMlSfKIFJtVmF0ViO4o4X89ZwsQjjHuYYDaB3el7iA63BzBlsC54Q7Ekv70/GI0UA3R3zJkMaBV12Z6NAE/kAgEJu9ZRcVm6MAIZInLwMU4R1frM0Bks1jeTe72agmxnAIrR8XDeAxzovbvXFwoxNyxiA63fPJGPVoGZq4ecfGvJ23i/Cg+cynB35lc3f+4QifpjCn+MxWkKCzCVEJXdDah19yXKlIxbaR1zm+YHkS0YSUzjr7NJUXHfDCrwAUpXpikfi2f9tgcXEnuhszScE1PCbdt22rRz1pS7MNdRxjCZ5j+8BQNRBLi2BjLGW14X3zd4d6ieoHWH+4fmbqU9dFsUgKN5qL4Gs2LZbbQwkf3+VbIRQK9RaSO9Hj+4/T0=
Public
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmy27XroKLfED3q32/K7G +TnREe2ZkSgceDJH9X+Jf2I++kJHxNxe5HbQBdTHW/tLTWxwMEpric9zGFlt1f76 zdG2iocGw81BVznN/btVAYJBGbhJPYTeULSCv4WG+NTrss8NSl6WGS9NCOKEWTA/ JjR1z8fXik5foTK18sLJloRFGmxcKV6ZI0VFEi77U6PouOseaPBRYgVlPAjNM/pl AuJotPjFYtNTQWCgpj+Vgt3cxm9erBl8G9K9rIsK6snNA1yEZT774CMLCnyovkd5 i55/5mIjGOdmy+x3qCYC2J+Xmssx56OebPyO8cAou8XQf5E/PMxBZ+8X5zuqnHza 2oK9Lo4K2hYVGpCBmG8WhCstYVvfxeb0cXifPOZnpiC4DrQ3q5atx7sH1V4OaAze eJ+nWKTKVaT9NLKEC3ObUNtLLjoh3AZr/RFh9OsYf3rmRFflJkswlVpfMQF6MAR4 CrDITaTdL0M5RWzE2/1Mh98p2HvTJXz0bFbcIfAvd3rAYku0P3OyO3EZ7KrpGXZa 4Mdu10GKEllk9bwCmDFHK/HMVzZPFK9RvKNpMyWchLCLO2gRxIHySn3lF/MHlBkq 0+DH3YM5L0EW92Uzu/IkZJ4o3z7YnrMHdVVN14bGlBfspn+t7LT2xTx3sWYQLm6r xYeQDSkiY24IqAiQzwdPmi0CAwEAAQ==
Private
MIIJKQIBAAKCAgEAmy27XroKLfED3q32/K7G+TnREe2ZkSgceDJH9X+Jf2I++kJH xNxe5HbQBdTHW/tLTWxwMEpric9zGFlt1f76zdG2iocGw81BVznN/btVAYJBGbhJ PYTeULSCv4WG+NTrss8NSl6WGS9NCOKEWTA/JjR1z8fXik5foTK18sLJloRFGmxc KV6ZI0VFEi77U6PouOseaPBRYgVlPAjNM/plAuJotPjFYtNTQWCgpj+Vgt3cxm9e rBl8G9K9rIsK6snNA1yEZT774CMLCnyovkd5i55/5mIjGOdmy+x3qCYC2J+Xmssx 56OebPyO8cAou8XQf5E/PMxBZ+8X5zuqnHza2oK9Lo4K2hYVGpCBmG8WhCstYVvf xeb0cXifPOZnpiC4DrQ3q5atx7sH1V4OaAzeeJ+nWKTKVaT9NLKEC3ObUNtLLjoh 3AZr/RFh9OsYf3rmRFflJkswlVpfMQF6MAR4CrDITaTdL0M5RWzE2/1Mh98p2HvT JXz0bFbcIfAvd3rAYku0P3OyO3EZ7KrpGXZa4Mdu10GKEllk9bwCmDFHK/HMVzZP FK9RvKNpMyWchLCLO2gRxIHySn3lF/MHlBkq0+DH3YM5L0EW92Uzu/IkZJ4o3z7Y nrMHdVVN14bGlBfspn+t7LT2xTx3sWYQLm6rxYeQDSkiY24IqAiQzwdPmi0CAwEA AQKCAgEAj4nc0IGL2vUenEMUvKS6vlwhrNC4BRIyS2hPMaH4QJFTKdBXbJxfVjsk rtAkXEv1Wrecir67/GyczQAj3heOTQXYMQk3U7Sv5Qw+I569wbiHmU/ix3n43nQq oRfVQqRJJUvqwkj91GvxeO92dr1vHFrYQwtar79RK92pedV9/LF67jcfhNDRHFP9 0RUOO07ZfPtXVMA+t0nAW6jUj2jlOKbPLd8TThel4kqML1uPY87vYcowq0aji2UD N/AheA6UibBxcumwuKIRm3C18dRRdLl3G1bZmjap2qVwBWSrq07sQC4GinrJl4yC eNJDm3UeKHHlKcrSEV6TILwLU9cV5CnfADzGIKVvyU6O9OWs2bk2r0w2pZ3VUJjC Wmm19S5gAWwAvgUEABnKODJGs28ttljaTOrgPlNMSEDVl56REyaD9Bl9Y7bjQop2 E7+F+9SiWYmb1sQz2/77zk3ZxtonAsVP7XixSW7hp0UZDur7Vo8XuzP5fnOP30c0 RWjlQwuixdtaYLavKP3W4HspTQL3jOa6Wq0zetcPv3rLYGXQ0L9fNhkA7AncO4Zi FGMBs4J7ReuCQQmWWb80DhBAQ7NN7kiZo7uuHLIGD1cQcg7KHycCu2OOBWrolq6r ZOY8I5tjjzEGGkmczcwkaArCVhiDBRW2m8TgqnYBEPsFgF/5FgECggEBANah1wjI R36bynDfEF2XyxCZFmvXdu5xPyhAgjbVsDTy0p5eWS+fBuxr574lt5cxUv4Alzv0 fdtuCaL/fEOe/bv8ZlSXzLZPkqdOpTOQqAKKXB05rLBhGMNkZjQDFAQkjY+SppSl 5AtdbIuhdhlbeyX7NwczbFVVh6ZnOdnU3rMNkLZoxEJUztFrPJBownRbRm+QQUp9 wxrZqKPiLhhKnTXfAvM1jrdlOarKpldrBsYxdTeuOP2gsij/RsGI/dhxLueAlCvi zsQzS94VgtLrJJ02ZEyZVqkGzGW+tYnvluydLFU9CXyC6jfw6eoZY+wTG3TRRbkR M7hJaj1Ov5xZsoECggEBALkWZXYj661GctJ54R+n2Ulm1r9gMXVsdmiqOOwmsqtA VKIks5ykhi0n05NJdan24+t5c9u8tP8Orq5qbhIBAUMQJtorRTntixJZa4oZ5lDC csSLKvTHKqcAnUwlL2sydy/IxvTsjRdnrEX8QV2oq40fb2tBI80XfBySDy7KEPdG bzI2/KbPaFZjphc5qNOV9BagvjqFmNO8DYyRHsSEnVyTuXOlkbJPvKIRNniNJRBI P0iFtwFtLZGUCMH7TK+9aKjBYizPAzklSf9/poeGluuKn5M0G4mvCCZVtOFw6p2Q 7j1jXUYQEcs9vgyobAfQNev/JLMjeGjaaXaV71nTea0CggEBAL6IGN4g/Oa14fZk 7qBHGer4G2FMerWdLpXK/k0zUSMP1EzmMIIHyBukhqrTzLCZBrWZTKfamMdsXX2n E2bsAw8YNrctsnq9FNEVDa5C4gKvVKpVAqno6BS8UcYmXWR4Fnq3ks0unsw/+RXT FYXZIe9LnUP1MFxoeu0Lgd2QDMoiZq6nPmIr6xUY/0Cq3sRwKozrICrCjaqOQhiJ tqW1xu2FtZa1mqXPZGvrTdMYnYDfctElBk6Qkte2FdfEhqPXhe3YxLBYvXiKmPTj X6lhOLWfDVa6YKXX9Sb1Ly7t06rks/BPKNaxWL6kTOKV+5AcPilrhVuOm70i3v7h o1NmhQECggEAaW6MlWOY2LeMqMCssK+YYuul4JYXFmCWgsCUdFEG7e5TR5nIhq5h kE9jgj8SO6Nb6cLhcIZqQ/BFKS2PTcoswdrthtGnOXxLAETXsW9XdyGM5tCvw4fA kCkVcU6tWE8C/cFNNC+bn3168NLlGUj/kAAcI+iTUDzUgiHhbDHGwFTq+pvAB/WV 5cAV2J0Lwptk0471TbjUeahhv3TbJe61BQtRVMM33270cQ2FDd65AjFlexZQTQu4 LXk6E+XmpSUr/RVLq2Kw31iScmxwnDratYndpKjGFwQRjGS+CL2dp+vrCiUT+Nkm ibO+Es/N2hWM4cYRTcoiyPfBo798/JoucQKCAQBw2Vm2CUbWC1IlgHU2rEngB1F1 c6asxmpIn3j4EiigwO+27G9cmpQ54CvRjp18Fw2/ZABok8C8edm+VMtWRd5gXFTP K7lmWJnGJ0W2eGcjdOCrHZx3sFxoer0Vdy3dQbcWtAQJhqUBbIqCwLkWIQgrsNdl CQiaeKqBz0cQrj6UkNs2qXfjzTg8xPgR/Yapps4O9yoJUKpVUiMlcHgRGi/wsgHx Mq/Ghvz6tYMW7zIXjgYw575Nd9BJy+si9dXShsFmwFQ0MoU0uHFI5oGTGvqc07j8 eVFNV+dm4dr9Irt0qhSHxcaVCyDs36bXz7S0kSgvECV1QhgtFQPOrVQdgsTn
Add -----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY----- to head and bottom of prviate base64 strings. than make private.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
|
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_v1_5 as Cipher_PKCS1_v1_5
from base64 import b64decode
enc ='''
NQr2MIa1jsaifAVOn3zYeMynNJwd4oBiiem4fJHsA1WjzfyhUp1+seCW0GMijoDHb3w9BMKj7aw6hhtae5/Qw5xOqMioJU3vvEj0BEHO1wInPqlOeTRdZb8BcTsXP+Z/KBA2FjSZcpGHo7rOZ7NtR15y3eY4s/e/tgKUHvPe9MdmDe1kINtyRXgjghJO9e3uMEQmFe2Ai5moVnG7yIVfUd3QG6/Z+K4PSttbJtjWSLFO7zpmYpEOg3XBxsOw/w5scJQqJ7OLGiH22u4+JFXRlD/wPmDzk9uYlLWLcCuxnY0xuMlSfKIFJtVmF0ViO4o4X89ZwsQjjHuYYDaB3el7iA63BzBlsC54Q7Ekv70/GI0UA3R3zJkMaBV12Z6NAE/kAgEJu9ZRcVm6MAIZInLwMU4R1frM0Bks1jeTe72agmxnAIrR8XDeAxzovbvXFwoxNyxiA63fPJGPVoGZq4ecfGvJ23i/Cg+cynB35lc3f+4QifpjCn+MxWkKCzCVEJXdDah19yXKlIxbaR1zm+YHkS0YSUzjr7NJUXHfDCrwAUpXpikfi2f9tgcXEnuhszScE1PCbdt22rRz1pS7MNdRxjCZ5j+8BQNRBLi2BjLGW14X3zd4d6ieoHWH+4fmbqU9dFsUgKN5qL4Gs2LZbbQwkf3+VbIRQK9RaSO9Hj+4/T0=
'''
rsa_key = RSA.importKey(open('private.txt', "rb").read())
cipher = Cipher_PKCS1_v1_5.new(rsa_key)
raw_cipher_data = b64decode(enc)
phn = cipher.decrypt(raw_cipher_data, None)
print(phn)
|
cs |
plain text : unknown-123-246-470-726.herokuapp.com/
|
1
2
3
4
5
6
7
8
|
s = [9,20,30,15,16,5,14,19,30,27,29,8,20,13,12,28]
ss = "0abcdefghijklmnopqrstuvwxyz[]. "
f = ""
for i in range(len(s)):
f+= ss[s[i]]
print f
|
cs |
it opens [.html]
Cryptography
15
Lhzdwt eceowwl: Dhtnwt Pcln Eaao Qwoohvw
Okw qsyo okcln bah'i fslo cl baht Dhtnwt Pcln dhtnwt cy yazwalw'y eaao ehlnhy. Dho sy co ohtly aho, okso zcnko dw fkso bah nwo. S 4vksllwt hmqasiwi s mkaoa slalbzahyqb oa okw ycow ykafvsycln kcy ewwo cl s mqsyocv dcl ae qwoohvw, fcok okw yosowzwlo: "Okcy cy okw qwoohvw bah wso so Dhtnwt Pcln." Sizcoowiqb, kw ksi ykawy al. Dho okso'y wgwl fatyw.
Okw mayo fwlo qcgw so 11:38 MZ al Xhqb 16, sli s zwtw ofwlob zclhowy qsowt, okw Dhtnwt Pcln cl rhwyocal fsy sqwtowi oa okw tanhw wzmqabww. So qwsyo, C kamw kw'y tanhw. Kaf ici co ksmmwl? Fwqq, okw DP wzmqabww ksil'o twzagwi okw WJCE isos etaz okw hmqasiwi mkaoa, fkcvk yhnnwyowi okw vhqmtco fsy yazwfkwtw cl Zsbecwqi Kwcnkoy, Akca. Okcy fsy so 11:47. Oktww zclhowy qsowt so 11:50, okw Dhtnwt Pcln dtslvk siitwyy fsy mayowi fcok fcykwy ae ksmmb hlwzmqabzwlo. Ecgw zclhowy qsowt, okw lwfy yosocal fsy valosvowi db slaokwt 4vksllwt. Sli oktww zclhowy qsowt, so 11:58, s qclp fsy mayowi: DP'y "Owqq hy sdaho hy" alqclw eathz. Okw eaao mkaoa, aokwtfcyw plafl sy wjkcdco S, fsy soosvkwi. Vqwgwqsli Yvwlw Zsnsuclw valosvowi okw DP cl rhwyocal okw lwjo isb. Fkwl rhwyocalwi, okw dtwspesyo ykceo zslsnwt ysci "Ak, C plaf fka okso cy. Kw'y nwoocln ectwi." Zbyowtb yaqgwi, db 4vksl. Laf fw vsl sqq na dsvp oa wsocln aht esyo eaai cl mwsvw.
tovm{v4T3Ehq_f1oK_3J1e_i4O4}
치환암호다.
quipqiup - cryptoquip and cryptogram solver
quipqiup.com
flag : rtcp{c4R3Ful_w1tH_3X1f_d4T4}
That's a Lot of Stuff...
Do you want some numbers? Here, take these numbers. I don't need them anyways. I have too many numbers at home, so go on, take them. Shoves numbers towards the computer screen
31 31 35 20 31 32 34 20 31 34 37 20 31 34 37 20 31 31 35 20 31 35 32 20 31 30 31 20 31 34 37 20 31 31 35 20 31 37 31 20 31 30 31 20 31 37 30 20 31 31 36 20 31 35 31 20 31 30 31 20 31 37 32 20 31 31 31 20 31 30 34 20 31 30 35 20 36 30 20 31 31 31 20 31 30 34 20 31 31 31 20 31 37 31 20 31 31 31 20 31 30 34 20 31 30 35 20 36 34 20 31 31 31 20 31 30 34 20 31 30 35 20 36 35 20 31 31 31 20 31 30 34 20 31 30 35 20 36 30 20 31 31 31 20 31 30 34 20 31 30 35 20 36 35 20 31 31 31 20 31 30 34 20 31 30 35 20 31 34 37 20 31 31 35 20 31 32 34 20 31 34 37 20 31 34 37 20 31 31 35 20 31 37 31 20 31 30 31 20 31 37 30 20 31 31 35 20 31 35 31 20 31 30 31 20 31 37 32 20 31 31 31 20 31 30 34 20 31 31 31 20 31 36 37 20 31 31 31 20 31 30 34 20 31 30 35 20 36 35
hex -> oct -> dec
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
task = '''36 31 20 36 31 20 36 34 20 34 30 20 36 31 20 36 31 20 36 36 20 34 30 20 37 31 20 37 31 20 34 30 20 36 31 20 36 31 20 36 32 20 34 30 20 36 31 20 36 32 20 36 33 20 34 30 20 37 31 20 37 31 20 34 30 20 36 34 20 37 30 20 34 30 20 36 31 20 36 31 20 36 30 20 34 30 20 36 31 20 36 31 20 37 30 20 34 30 20 36 35 20 36 31 20 34 30 20 36 31 20 36 31 20 36 34 20 34 30 20 36 31 20 36 31 20 36 35 20 34 30 20 36 34 20 37 31 20 34 30 20 36 34 20 37 30 20 34 30 20 36 31 20 36 31 20 36 30 20 34 30 20 36 31 20 36 31 20 36 35 20 34 30 20 37 31 20 36 35 20 34 30 20 37 31 20 36 37 20 34 30 20 36 31 20 36 31 20 36 34 20 34 30 20 36 35 20 36 31 20 34 30 20 37 31 20 36 35 20 34 30 20 36 35 20 36 32 20 34 30 20 37 31 20 36 35 20 34 30 20 37 31 20 37 31 20 34 30 20 36 34 20 37 30 20 34 30 20 36 34 20 37 30 20 34 30 20 36 37 20 36 36 20 34 30 20 37 31 20 36 35 20 34 30 20 37 31 20 37 31 20 34 30 20 36 35 20 36 32 20 34 30 20 36 31 20 36 31 20 36 36 20 34 30 20 36 31 20 36 31 20 36 35 20 34 30 20 36 31 20 36 32 20 36 35'''
task = task.replace(" ", ",")
print task
###
a = [36,31,20,36,31,20,36,34,20,34,30,20,36,31,20,36,31,20,36,36,20,34,30,20,37,31,20,37,31,20,34,30,20,36,31,20,36,31,20,36,32,20,34,30,20,36,31,20,36,32,20,36,33,20,34,30,20,37,31,20,37,31,20,34,30,20,36,34,20,37,30,20,34,30,20,36,31,20,36,31,20,36,30,20,34,30,20,36,31,20,36,31,20,37,30,20,34,30,20,36,35,20,36,31,20,34,30,20,36,31,20,36,31,20,36,34,20,34,30,20,36,31,20,36,31,20,36,35,20,34,30,20,36,34,20,37,31,20,34,30,20,36,34,20,37,30,20,34,30,20,36,31,20,36,31,20,36,30,20,34,30,20,36,31,20,36,31,20,36,35,20,34,30,20,37,31,20,36,35,20,34,30,20,37,31,20,36,37,20,34,30,20,36,31,20,36,31,20,36,34,20,34,30,20,36,35,20,36,31,20,34,30,20,37,31,20,36,35,20,34,30,20,36,35,20,36,32,20,34,30,20,37,31,20,36,35,20,34,30,20,37,31,20,37,31,20,34,30,20,36,34,20,37,30,20,34,30,20,36,34,20,37,30,20,34,30,20,36,37,20,36,36,20,34,30,20,37,31,20,36,35,20,34,30,20,37,31,20,37,31,20,34,30,20,36,35,20,36,32,20,34,30,20,36,31,20,36,31,20,36,36,20,34,30,20,36,31,20,36,31,20,36,35,20,34,30,20,36,31,20,36,32,20,36,35]
flag = ""
for aa in a:
flag += chr(int(str(aa), 16))
flag = flag.replace(" ", ",")
print flag
###
b = [61,61,64,40,61,61,66,40,71,71,40,61,61,62,40,61,62,63,40,71,71,40,64,70,40,61,61,60,40,61,61,70,40,65,61,40,61,61,64,40,61,61,65,40,64,71,40,64,70,40,61,61,60,40,61,61,65,40,71,65,40,71,67,40,61,61,64,40,65,61,40,71,65,40,65,62,40,71,65,40,71,71,40,64,70,40,64,70,40,67,66,40,71,65,40,71,71,40,65,62,40,61,61,66,40,61,61,65,40,61,62,65]
flag = ""
for bb in b:
flag += chr(int(str(bb), 8))
flag = flag.replace(" ", ",")
print flag
###
c = [114,116,99,112,123,99,48,110,118,51,114,115,49,48,110,115,95,97,114,51,95,52,95,99,48,48,76,95,99,52,116,115,125]
flag = ""
for cc in c:
flag += chr(int(str(cc), 10))
print flag
|
cs |
General Skills
Treeeeeeee
It appears that my cat has gotten itself stuck in a tree... It's really tall and I can't seem to reach it. Maybe you can throw a snake at the tree to find it?
Oh, you want to know what my cat looks like? I put a picture in the hints.
Hints
Here, my cat looks like this:
#FFC90E#000000#FFC90E#FFFFFF#FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF #FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFC90E#FFC90E#FFC90E#FFC90E#FFC90E#FFFFFF#FFFFFF #FFFFFF#FFFFFF#FFFFFF#FFC90E#FFFFFF#FFC90E#FFFFFF#FFFFFF#FFFFFF
Bigtree/ has 29,185 items, totalling 116.2 MB.
수많은 폴더에 jpg 파일들이 숨어있다.
To gather .jpg files in one folder, I used find & exec command.
bigtree$ find . -type f -name "*.jpg" -exec mv {} ./flag \;
All of .jpg files move to ./flag/
Now, easily find flag file which has different file size.
flag file : 2.2KB
others : 1.5KB, 1.7KB
'CTF Write Up' 카테고리의 다른 글
| angstrom CTF 2020 write up (0) | 2020.03.14 |
|---|---|
| UTCTF 2020 Write up (0) | 2020.03.07 |
| Christmas CTF 2019 Write-up 문제 풀이 (2) | 2019.12.30 |
| UTC-CTF 2019 Teaser write-up (0) | 2019.12.22 |
| X-MAS CTF 2019 X-MAS Helper write-up (0) | 2019.12.21 |