| Toolkit | basic | 25 | General Information |
Is a computer forensics distribution that installs all necessary tools on Ubuntu to perform a detailed digital forensic and incident response examination.
google search.
| Little Story Boy | basic | 25 | Digital Forensics |

extract LSB data
you can use zsteg.
| Light | easy | 50 | Digital Forensics |
Just get the flag
file : light

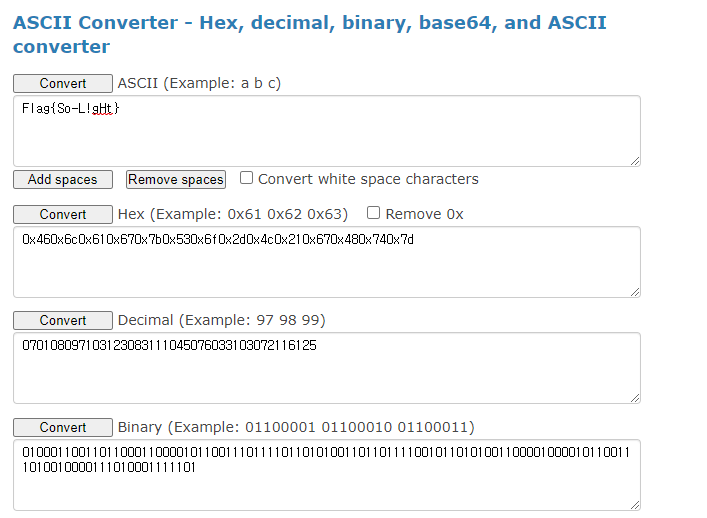
This file has png header signature. Therefore It is PNG file, and it has also png footer signature.

After PNG footer signature, there are some binary strings.
I could guess that binary is ascii code, because it starts 01~~.
easy.
| Meta Header | easy | 50 | Digital Forensics |
Can You help us to extract the metal from Exchangeable header
file : metal.jpg

image description is strange.
hmm
next!
| volatility | easy | 50 | Digital Forensics |
welcome to volatility 101, you have to know when you start analyzing a memory dump you have to look to processes and files on desktop.
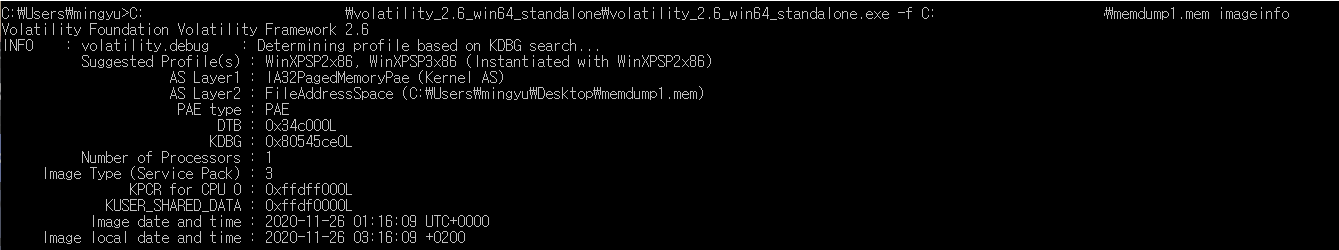
profile = WinXPSP2x86
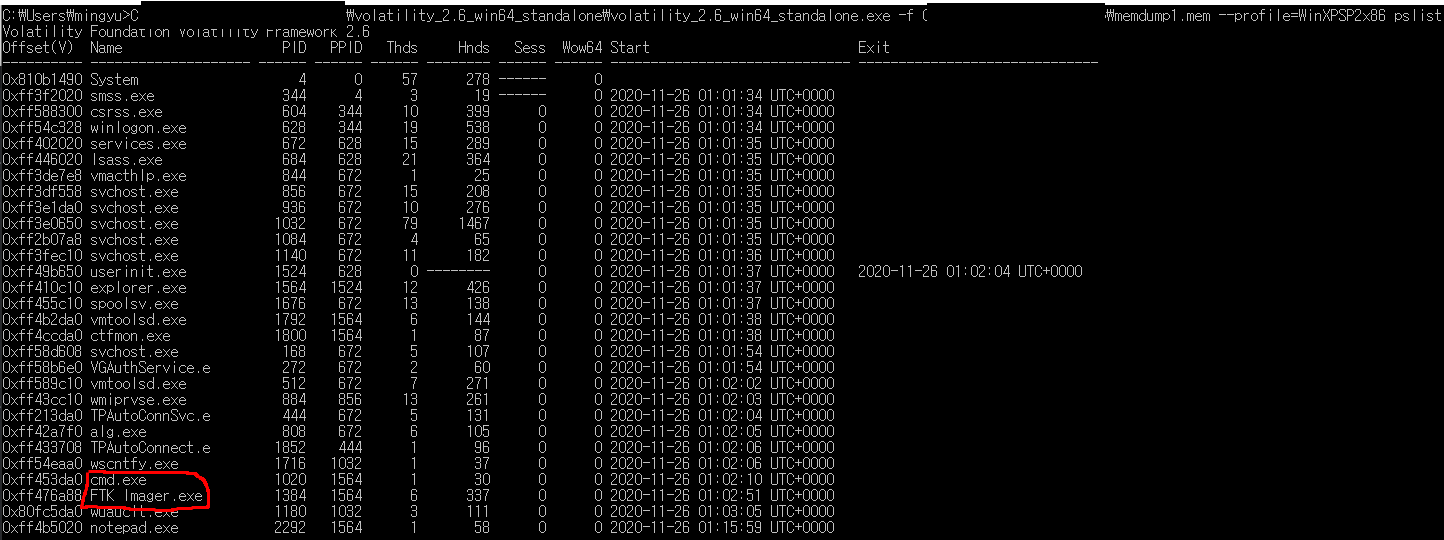
프로세스 특이사항은 이정도.

/Desktop/flag/

나오는게 없다. R-studio로 분석해봐야 할 거 같다.

another memdumpfile in Desktop dir.

There are 3 files which has 0 byte size in flag dir.
The file name seems like 'key'.
compare with look_to_clipboard.txt and filename.
k.08462 -> 20
e.22743 -> 8
y.08981 -> 40
이 다음은 mem을 추출해봐야 할거 같다.




아 easy 맞냐고
| Dega | hard | 200 | Digital Forensics |
Dega Company has been attacked and some data have been exfiltrated, Help them to know what exactly has been leaked.
pcap
base64로 인코딩된 문자열이 많던데
| last human | hard | 200 | Digital Forensics |
This Stream is so weird, looking something hidden here!!
sonic visualizer - failed
audio lsb - failed
-롸업-
0xmohammed.github.io/2020/11/29/Last-Human-Writeup.html
'Last human' writeup CyberTalents DF CTF - 0xMohammed
Description This Stream is so weird, looking something hidden here!! Diffculity: Hard Walkthrough Challange is a wave file with high pitched noise, After examining file with usual tools (binwalk, exiftool, strings,..etc) we found nothing so we should dig d
0xmohammed.github.io
| Xmen | medium | 100 | Digital Forensics |
cyber Criminal is hiding information in the below file .can you capture the flag ?. Note: Flag format flag{XXXXXXX}
00000000: 504b 0304 0a00 0900 0000 e52b 944d d66f PK.........+.M.o
00000010: ef86 2300 0000 1700 0000 0a00 1c00 7365 ..#...........se
00000020: 6372 6574 2e74 7874 5554 0900 036d 6f1b cret.txtUT...mo.
00000030: 5c6d 6f1b 5c75 780b 0001 0400 0000 0004 \mo.\ux.........
00000040: 0000 0000 89ed 4cbb 8ba3 91b4 8e10 d9e5 ......L.........
00000050: ab2e 196e 20f4 37df fbe5 096c ed4e 8d0a ...n .7....l.N..
00000060: e056 e98c 26b1 a450 4b07 08d6 6fef 8623 .V..&..PK...o..#
00000070: 0000 0017 0000 0050 4b01 021e 030a 0009 .......PK.......
00000080: 0000 00e5 2b94 4dd6 6fef 8623 0000 0017 ....+.M.o..#....
00000090: 0000 000a 0018 0000 0000 0001 0000 00a4 ................
000000a0: 8100 0000 0073 6563 7265 742e 7478 7455 .....secret.txtU
000000b0: 5405 0003 6d6f 1b5c 7578 0b00 0104 0000 T...mo.\ux......
000000c0: 0000 0400 0000 0050 4b05 0600 0000 0001 .......PK.......
000000d0: 0001 0050 0000 0077 0000 0000 00 ...P...w.....
xxd -r garbage garbage.zip
password brute-force 1to5 char - failed
lock bit change - failed
----풀이보고 내용추가----
dictionary attack으로 패스워드는 hacker_crackdown가 됨.;;
| Habibamod | medium | 100 | Digital Forensics |
Habibamod is sending a secret signal, tune your receiver.

It's simple.

Value of encoder is encoded in base64.

0 to . , 1 to !
To decode it: . to 0, ! to 1.
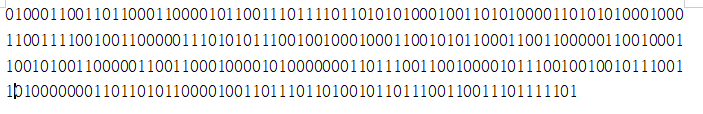
Bin to ascii

good.
| Location | medium | 100 | Digital Forensics |
vcan0 06C [8] 88 E6 0A 3D EC DC 50 2A
| Bomp | medium | 100 | Digital Forensics |
Why dosen't my BOMP Explode!!
Format: Flag{}
b0mp 파일이 주어진다.
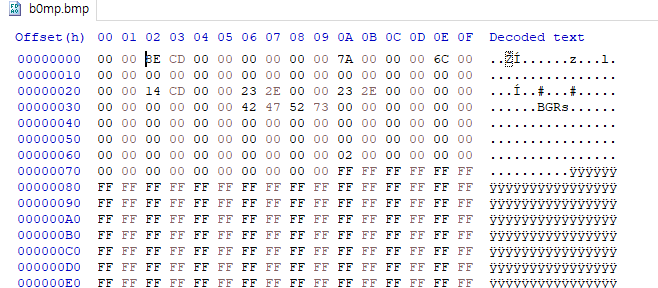
first 2 bytes are empty, but next 4 bytes seems like file size.
0xcdbe = 52670 =

so this is bmp file. b0mp에서 0을 빼면 bmp이기도 하다.
put 0x42 0x4D (bmp magic number) into first 2 bytes.

hmm

another bits are also empty.

----풀이보고 내용추가----
b0mp의 파일명을 b0mp.data로 바꾸고 GIMP에 불러온 뒤에, 오프셋, 너비, 높이를 아래와 같이 조절하면 플래그를 확인할 수 있다.

| P@dly | medium | 100 | Digital Forensics |
Someone outside the department has downloaded some files from our server but fortunately we encrypt all the files. Can you get this files?

note.epd and readme.txt were transferred.
pub is directory.
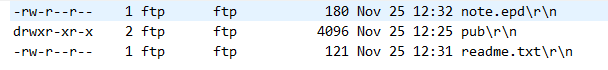

note.epd is encrypted file.
How to decrypt note.epd.
xor 0~0xff - failed
'CTF Write Up' 카테고리의 다른 글
| 0xL4ugh CTF write up (0) | 2021.01.16 |
|---|---|
| 2020 Christmas CTF [show me the pcap] Write-up (2) | 2020.12.27 |
| 제 2회 TeamH4C CTF 2020 Write-up (0) | 2020.10.13 |
| CCE2020 Quals Write-up (0) | 2020.09.26 |
| FIESTA 2020 Write up (2) | 2020.09.07 |