Forenscis


3Cd7MMS7GmZMwxmRTfQwoXvxcDkGt8o4cFzwPUrg
then what?
아 base58이었넹
ah it was base58 encoded strings.


ascii 85 -> pastebin.pl/view
use "d02a7960"
pastebin.pl/view/d02a7960



morse code

S0METIM35SH4RK1SFR13ND1Y


png file.
4F -> 4E
43 -> 44

46 -> 4e

nothing here :(


move to 5527125



xor 6

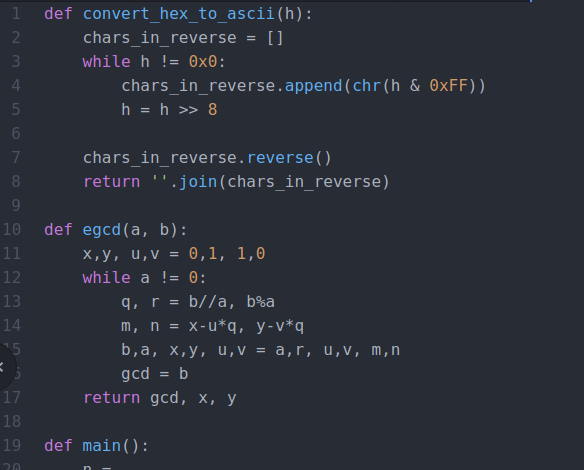
Crypto

{ ^),!&),!!$,^$,!^%,!$&,!%),!&#,!!#,^#,!&!,!$@,^),!$!,!^@,!$$,!#&,^!,!^#,!#&,!!),^#,!!$,!@),!)^,!@%,^!,^!,!&% }
! -> 1
@ -> 2
# -> 3
...
60 170 114 64 165 147 150 173 113 63 171 142 60 141 162 144 137 61 163 137 110 63 114 120 106 125 61 61 175
hmm..
Isn't it this?
아 8진수였네
ah octal..
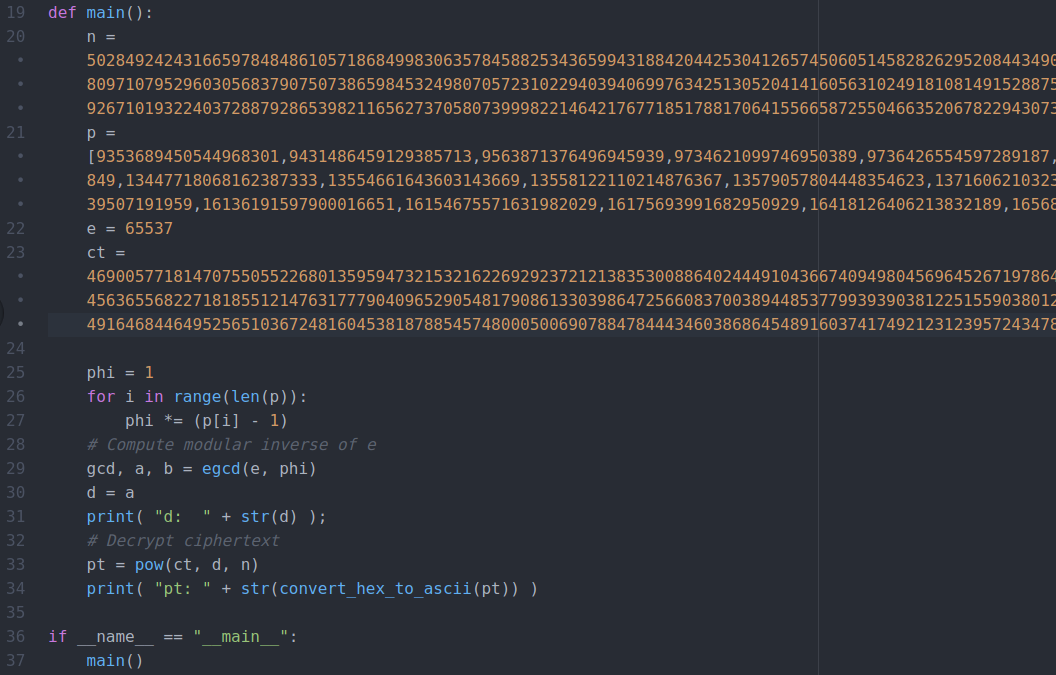
n = 5028492424316659784848610571868499830635784588253436599431884204425304126574506051458282629520844349077718907065343861952658055912723193332988900049704385076586516440137002407618568563003151764276775720948938528351773075093802636408325577864234115127871390168096496816499360494036227508350983216047669122408034583867561383118909895952974973292619495653073541886055538702432092425858482003930575665792421982301721054750712657799039327522613062264704797422340254020326514065801221180376851065029216809710795296030568379075073865984532498070572310229403940699763425130520414160563102491810814915288755251220179858773367510455580835421154668619370583787024315600566549750956030977653030065606416521363336014610142446739352985652335981500656145027999377047563266566792989553932335258615049158885853966867137798471757467768769820421797075336546511982769835420524203920252434351263053140580327108189404503020910499228438500946012560331269890809392427093030932508389051070445428793625564099729529982492671019322403728879286539821165627370580739998221464217677185178817064155665872550466352067822943073454133105879256544996546945106521271564937390984619840428052621074566596529317714264401833493628083147272364024196348602285804117877
e = 65537
c = 4690057718147075505522680135959473215321622692923721213835300886402444910436674094980456964526719786485709929645871497583481786451712108343985733309427211434750949557522557087475715799166136616546091244246093209194216096205011115055709130990240778725741521267153888212132276867942685123502211572949952162376597662509054070693025973089923370015547373862589488928782901235791144433788299046705518327561160954291094820233386528023713184029738780555483600166071578613803010858511582163397706626459433456365568227181855121476317779040965290548179086133039864725660837003894485377993939038122515590380127757353399577646033195886942935498851291625325622687406058565345707842924577200871090281931390828399034387159796711570518912284855782049322766568438776035673997640836043767460584670094065481165095303859142188605921710309909549354356478577687136627040919972987279885429990570784611705563443122226291405511409355924588407638851356402686178076614729462505897314633054448103933929160379080620408454649164684464952565103672481604538187885457480005006907884784443460386864548916037417492123123957243478299871616131317172973941585334012558762947082226744473068190488648000780008598569174088053018903156614111943478152720349210983651343
search n at www.factordb.com/
factordb.com
www.factordb.com

good.




0xL4ugh{I_Th1nk_Br1ll3_W45_$m4rt}
Web


make money~

I found base32 strings in cookie.


Reverse Engineering


HxD



WA! Flag!


rand() % 4 값을 반복 생성하여 파일 크기와 동일한 크기의 배열에 저장한다.
파일의 j번째 바이트와 랜덤값이 들어간 배열의 j번째 바이트를 가져와서
mystery함수 호출
Repeat generation of values (rand() %4) and push them on an array of the same size as the file size.
Gets the jth byte of the file and the jth byte of the array containing random values.
call mystery function

랜덤값이 2또는 0인경우 파일의 값과 1을 xor연산하여 리턴.
If the random value is 2 or 0, xor computes the byte and 1 of the file and returns it.
main 함수에서 srand(0)을 사용했으므로 시드가 고정.
랜덤값을 구할 수 있음.
The seed is fixed because it used sand(0) in main func.
I can get random values.


Programming




Misc

Sonic Visualiser
spectrogram

FLAG : 0xL4ugh{SP3c7ro_1s_Gr347}

github.com/jzyra/DecodeAndroidGesture
jzyra/DecodeAndroidGesture
This tool decode Android's pattern lock screen with gesture.key file in Android device. - jzyra/DecodeAndroidGesture
github.com


ribt/dtmf-decoder
Extract phone numbers from an audio recording of the dial tones. - ribt/dtmf-decoder
github.com


66#666#8#33#888#33#777#999#8#44#444#66#4#666#66#7777#2#6#33#9#2#999#
->
noteverythingonsameway
'CTF Write Up' 카테고리의 다른 글
| starCTF 2021 write-up (0) | 2021.01.18 |
|---|---|
| The Cyber Grabs CTF 0x02 write up (0) | 2021.01.17 |
| 2020 Christmas CTF [show me the pcap] Write-up (2) | 2020.12.27 |
| CyberTalents Digital Forensics CTF write up (0) | 2020.11.29 |
| 제 2회 TeamH4C CTF 2020 Write-up (0) | 2020.10.13 |