반응형

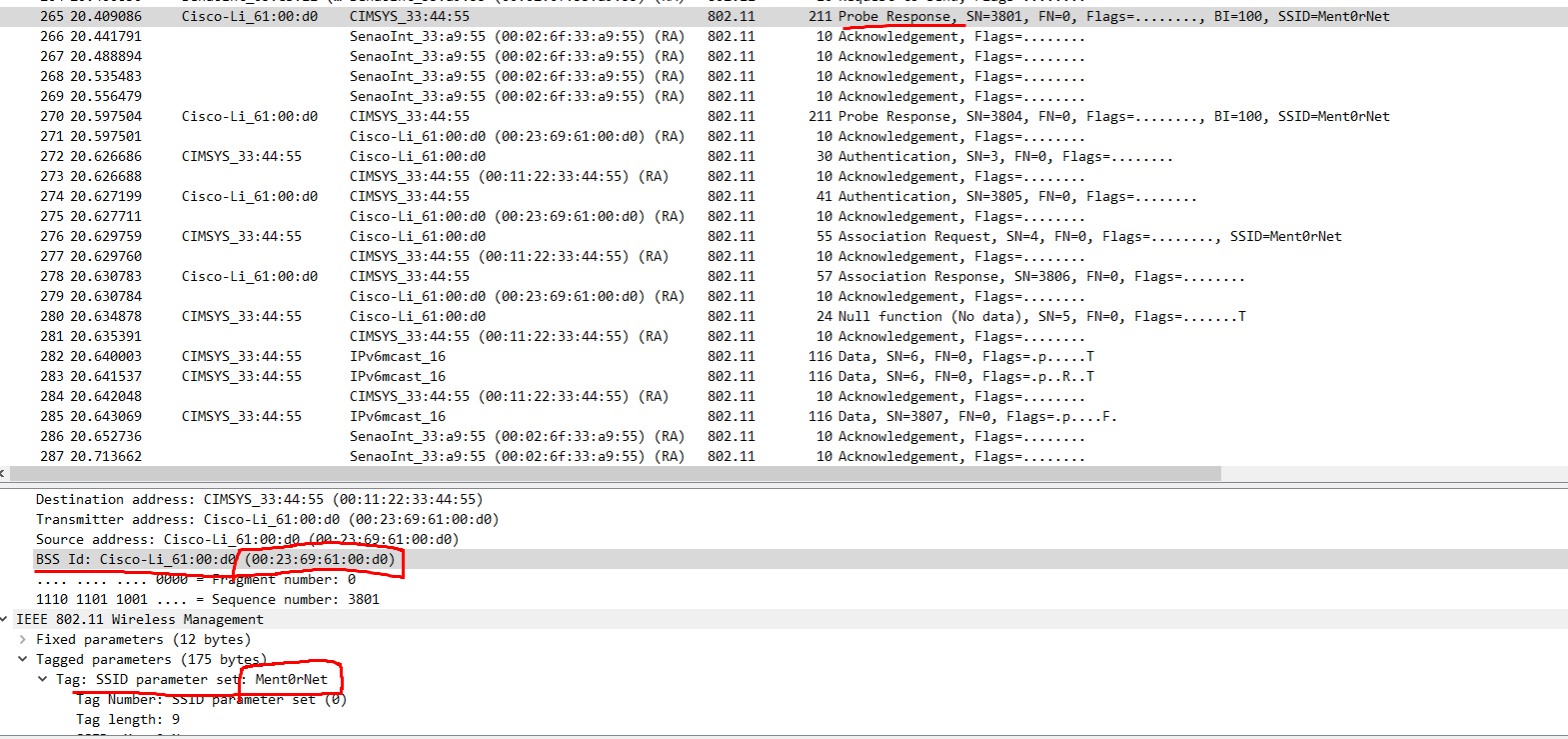
Ment0rNet/00:23:69:61:00:d0


413.576954

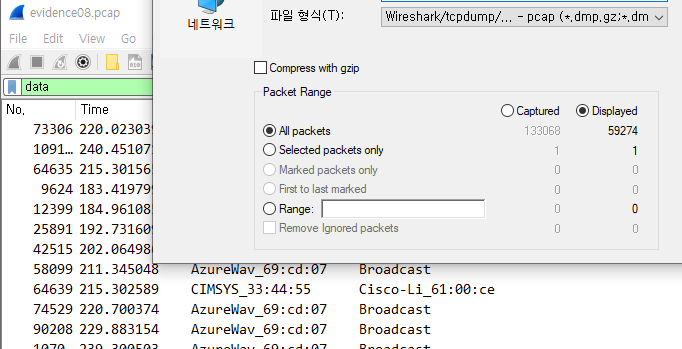
59274

$tshark -r evidence08.pcap -Y '(wlan.bssid == 00:23:69:61:00:d0) && wlan.wep.iv' -T fields -e wlan.wep.iv | sort -u | wc -l
29719
aircrack-ng
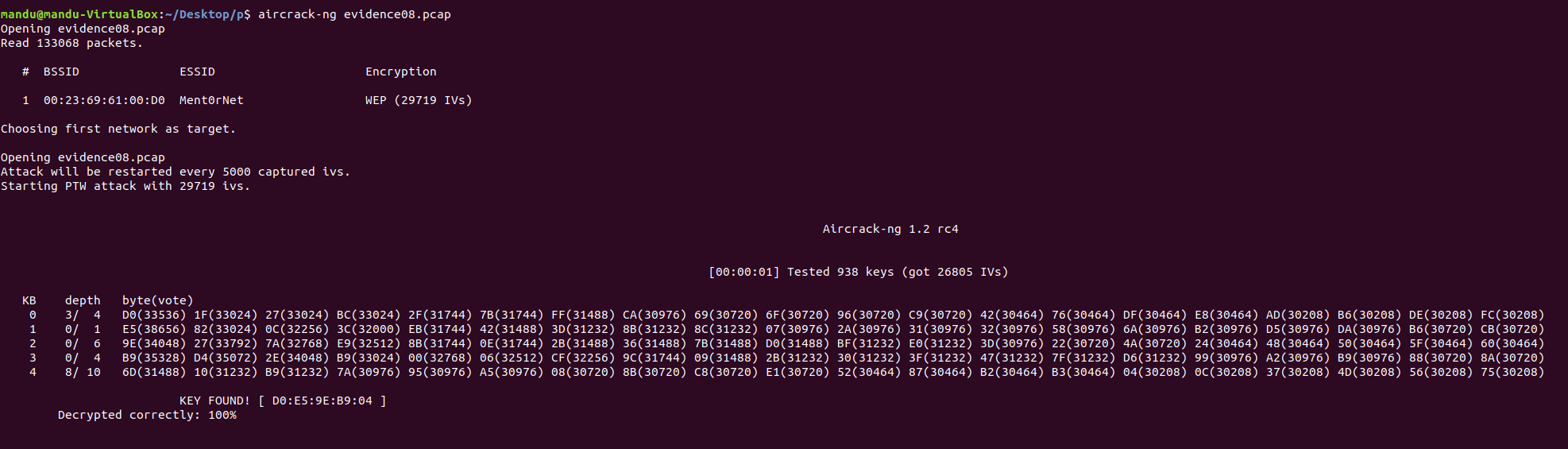
crack key
airdecap-ng

decrypt
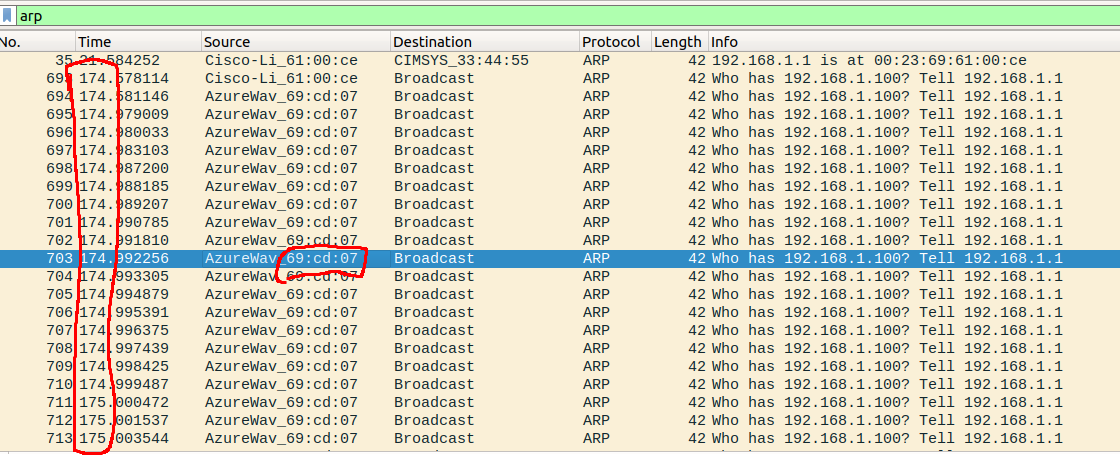
arp

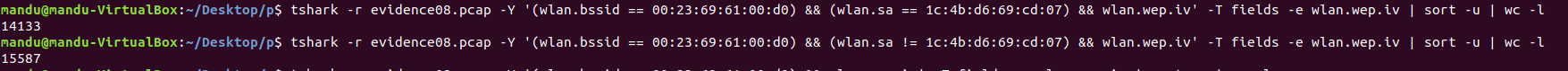
공격자 : tshark -r evidence08.pcap -Y '(wlan.bssid == 00:23:69:61:00:d0) && (wlan.sa == 1c:4b:d6:69:cd:07) && wlan.wep.iv' -T fields -e wlan.wep.iv | sort -u | wc -l
그외 : tshark -r evidence08.pcap -Y '(wlan.bssid == 00:23:69:61:00:d0) && (wlan.sa != 1c:4b:d6:69:cd:07) && wlan.wep.iv' -T fields -e wlan.wep.iv | sort -u | wc -l



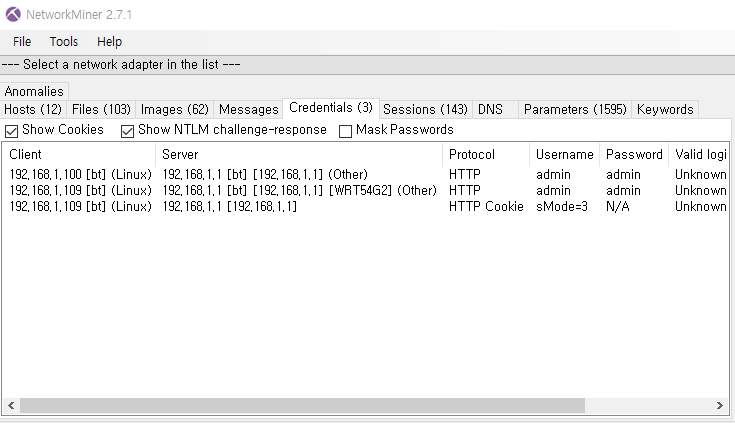
admin:admin


반응형
'WAR GAME > [DigitalForensic] with CTF' 카테고리의 다른 글
| CTF-D [Sans Network Forensic [Puzzle 3] #1~#6] (0) | 2021.08.04 |
|---|---|
| CTF-D [Sans Network Forensic [Puzzle 3] #1~#8] (0) | 2021.07.08 |
| D-CTF [DefCoN#22 #1] (0) | 2021.07.08 |
| D-CTF [DefCoN#21 #1] (0) | 2021.07.06 |
| D-CTF [Find Key(WhiteHat)] (0) | 2021.07.04 |