롸업 보고 다시 푼 문제 풀이 포함
Intro : Knock Knock
Author: Braguette#0169
We have to monitor our network every day to make sure our admins don't help players get out of the game.
We are sending you a suspicious capture. Do your job !
check Host IP : 192.168.157.185
convert pcapng to pcap using editcap
Use NetworkMiner
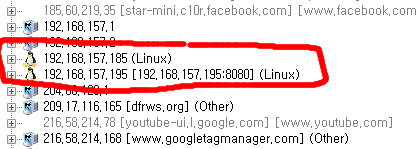
Private IP network
target IP : 192.168.157.195
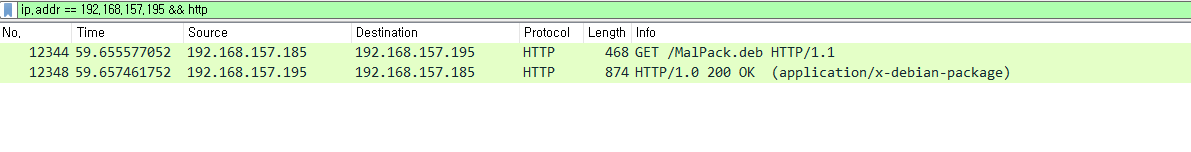
something suspicious
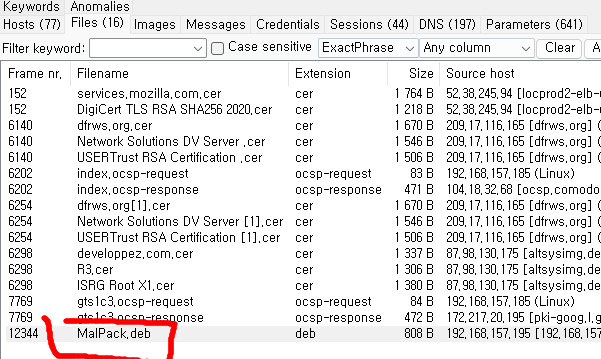
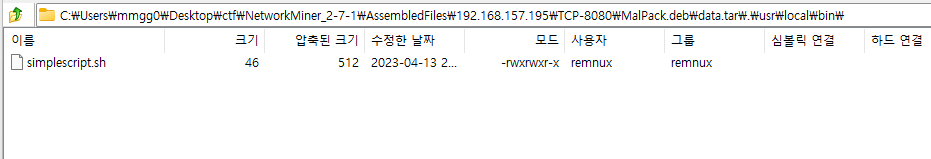
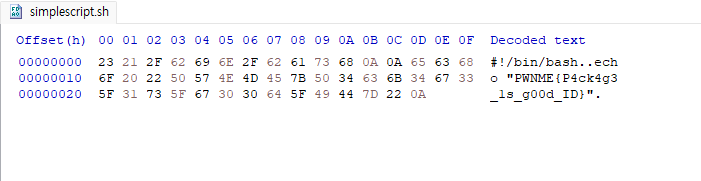
Easy : Free flag

Author: Braguette#0169
A few hours after installing the malicious package. We could notice that the traffic became weird again. Thanks to you, we know that our admin would have been compromised, we fear exfiltration! Do your job !pcap파일이 주어진다.
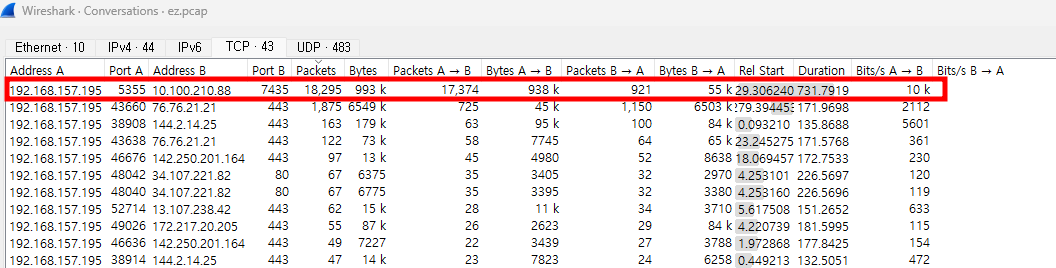
conversations를 보면, 192.168.157.195:5355 에서 10.100.210.88:7435로 대량의 패킷이 전송되었음을 확인할 수 있다.
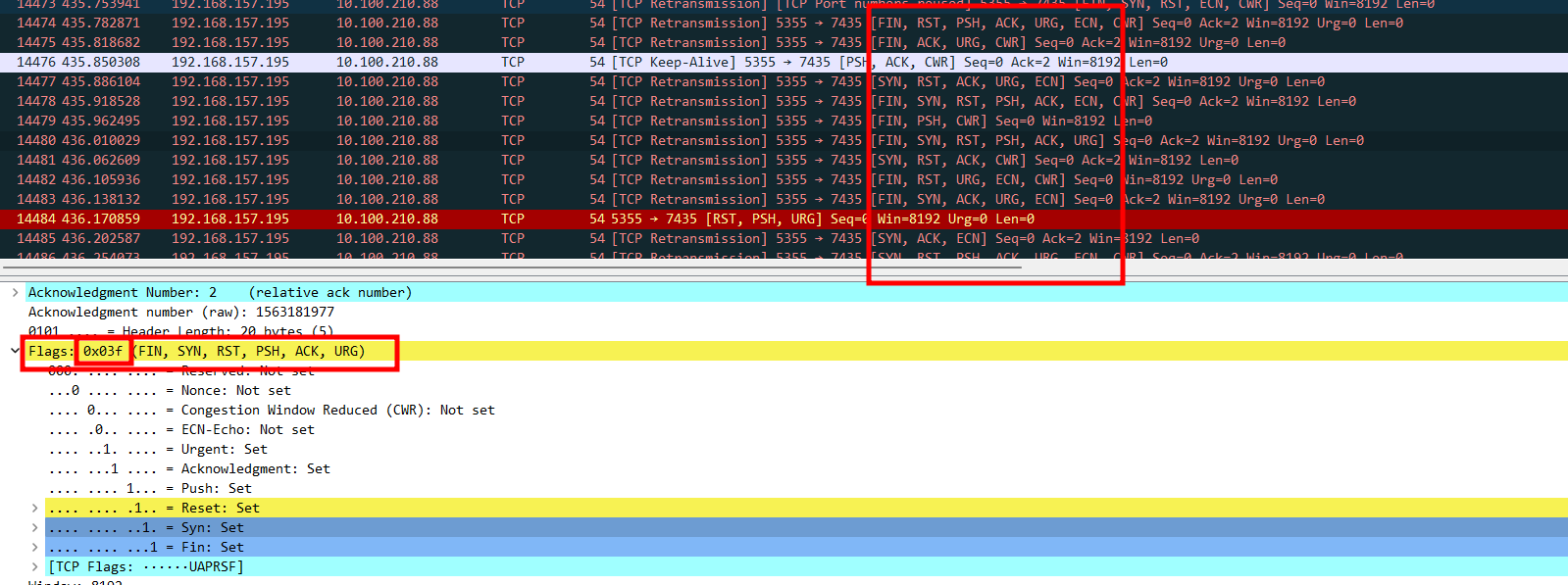
해당 패킷들을 보면 TCP Flags 값들이 계속 변화하는 것을 알 수 있다.
문제 이름이 Free Flag 인 것도 TCP flag를 보라는 힌트인 것 같다.
해당 FLAG들을 추출하기 위해서 tshark를 사용한다.
tshark -r ez.pcap -Y 'ip.src==192.168.157.195 && tcp.srcport==5355 && ip.dst==10.100.210.88 && tcp.dstport==7435' -T fields -e tcp.flags | cut -c 5-| xxd -r -p > a.7z

앞에 두 바이트만 지워주면 7z파일이 된다.

Medium : Silver


Author: Mr.NOODLE#9112
Hey,
I received a flash drive in my mailbox. It appears that the person who sent me the package was aware that I was using Linux. However, the flash drive self-destructed before I was able to make an image of it. To get the flag, you have to go to the showcase site of the c2 in question.
This is real malware, so be careful when running it, use a vm for malware analysis
Checksum Sha256 of usb_drive.img : 8947e34165792040d86915aea29df01f5e65f49ccfd624032522720ffb87c379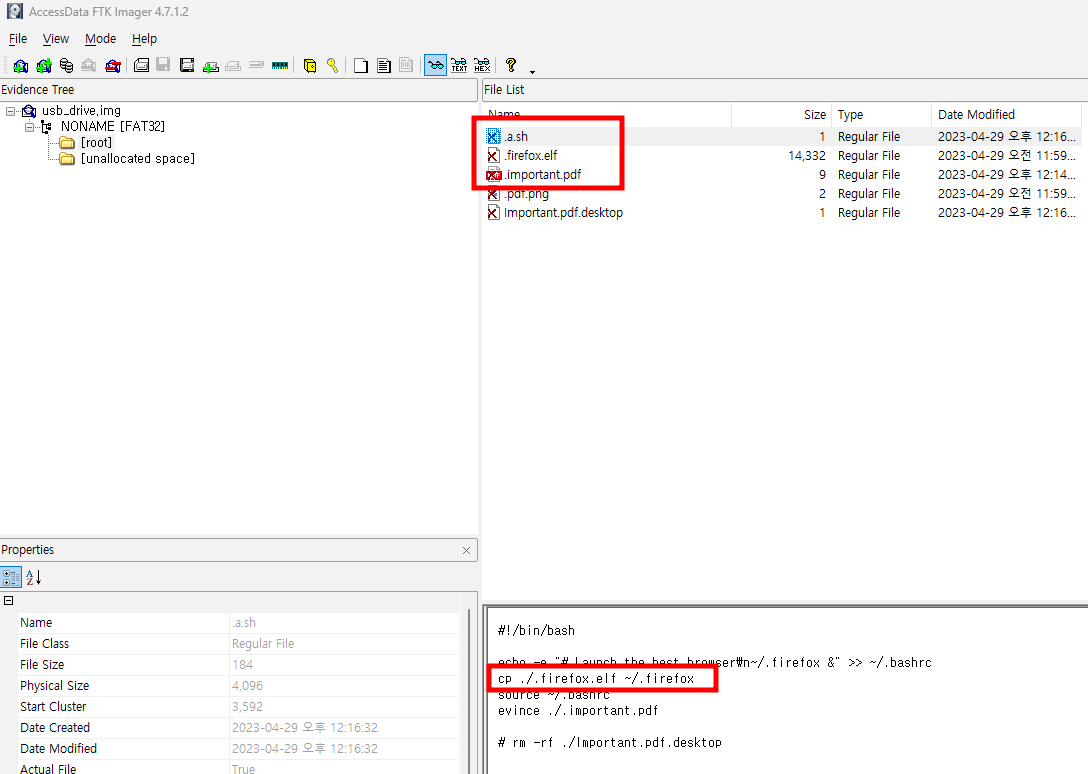
.firefox.elf가 악성파일로 의심된다. (추출해내면 Windows Defender가 탐지해낸다.)
해당 악성 파일을 IDA로 까보면 복잡하게 생겼다. 해당 파일을 리버싱하라고 준 건 아닐거고 C2 서버만 알아내면 되기 때문에, 가상 머신에서 해당 악성프로그램을 실행해서 패킷만 따내면 된다.
하지만 더 편한 바이러스토탈을 사용했다.
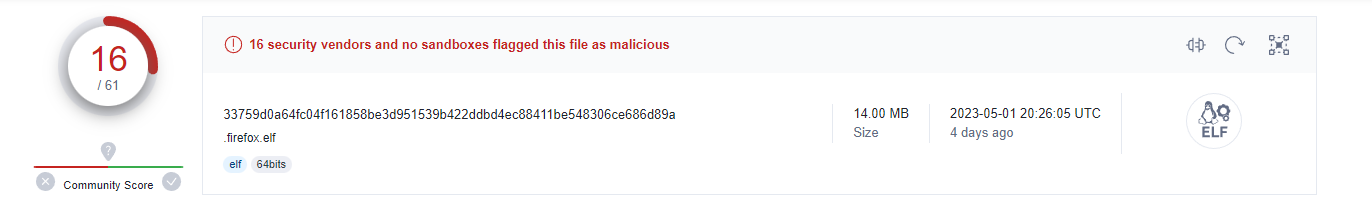
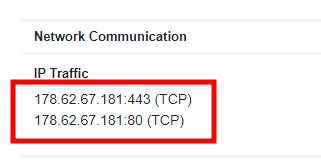
해당 ip로 접속하면 플래그가 나온다.

Medium : Compromised
-> hardcore


Author: rayanlecat#2609
Description :
An attacker has successfully compromised your company and more specifically your Active Directory! Your role is to find all the persistence techniques that the attacker has used in order to apply countermeasures.
Format :
The flag should be submitted in the following form: PWNME{persistence1user1-persistence2user2-persistence3user3-persistence4user4}
Where persistence is the name of the technique in lower case and user is the samAccountName of the user impacted in lower case.
The persistence techniques need to be put in chronological order of usage in the Active Directory.
Exemple :
PWNME{scheduletaskjessie_vaughan-createaccountmagdalena_gonzales-goldenticketjordan_gates-adminsdholderjaclyn_huber}
Important :
If you think that you found the right methods of persistence and you have an issue, please open a ticket on Discord so an administrator can validate your entry.
File :
https://drive.google.com/file/d/1tVBP05eKJbR6kswl6k-DeVRQ3x_e4CFk/view?usp=sharing
Hard : TimmyIsDump
-> medium



Author: Braguette#0169
Our administrator Timmy is a bit of an idiot, but that's why we love him. However, he downloaded a script that did something weird to our Detention user database. Since we know he's not the brightest, we make sure to do regular memory dump. I know you are the best. Get the file
File : https://drive.proton.me/urls/V7EC0VYPKC#XMtRuMT5uYy9lime 확장자의 메모리 덤프가 주어진다.
lime이 사용된 것으로보아, 리눅스 환경으로 추측된다.

fedora 22.x64 버전이며, 커널 버전은 4.2.6-200이다.
환경 구축을 위해서 fedora 22 x64버전의 iso를 다운받아 가상머신에 설치한다.
https://dl.fedoraproject.org/pub/archive/fedora/linux/releases/22/Workstation/x86_64/iso/
sudo dnf install kernel-4.2.6-200.fc22.x86_64.rpm \
kernel-core-4.2.6-200.fc22.x86_64.rpm \
kernel-devel-4.2.6-200.fc22.x86_64.rpm \
kernel-headers-4.2.6-200.fc22.x86_64.rpm \
kernel-modules-4.2.6-200.fc22.x86_64.rpm \
kernel-modules-extra-4.2.6-200.fc22.x86_64.rpm \
kernel-tools-4.2.6-200.fc22.x86_64.rpm \
kernel-tools-libs-4.2.6-200.fc22.x86_64.rpm \
kernel-tools-libs-devel-4.2.6-200.fc22.x86_64.rpm
이후는 볼라티리티 프로필을 생성해서 볼라티리티로 분석
'CTF Write Up' 카테고리의 다른 글
| Codegate2023 quals [n³] (0) | 2023.06.26 |
|---|---|
| 2023 핵테온 세종 본선 문제 리뷰 (0) | 2023.05.12 |
| 제8회 BoB 정보보안 CTF(BISC) (5) | 2022.09.09 |
| San Diego CTF 2022 Forensics write up (0) | 2022.05.09 |
| NahamCon CTF 2022 Forensic Write up (0) | 2022.04.30 |