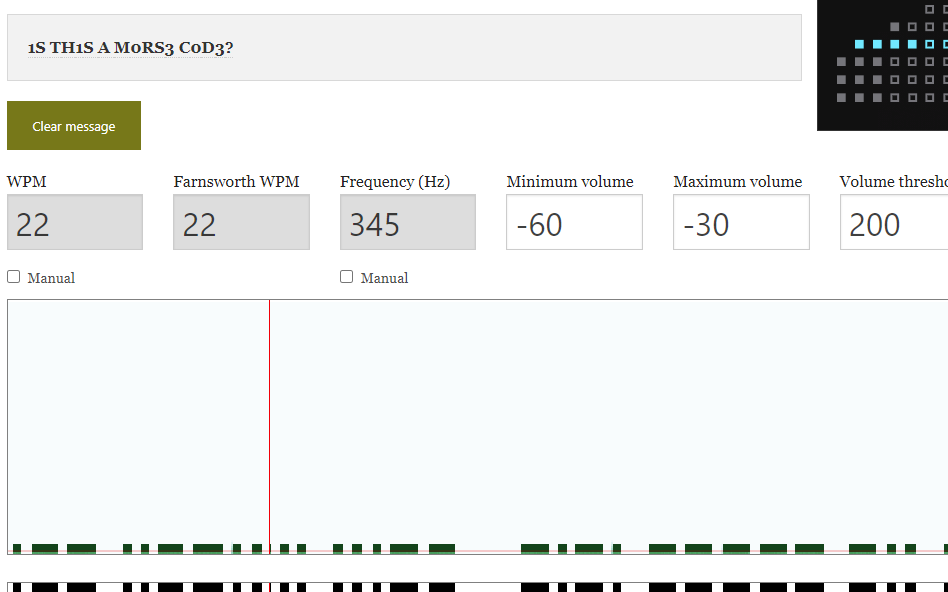
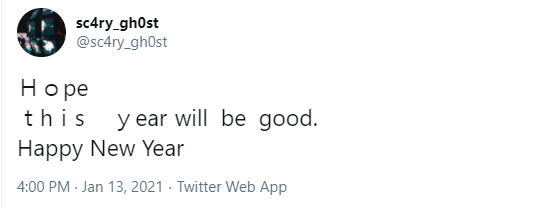
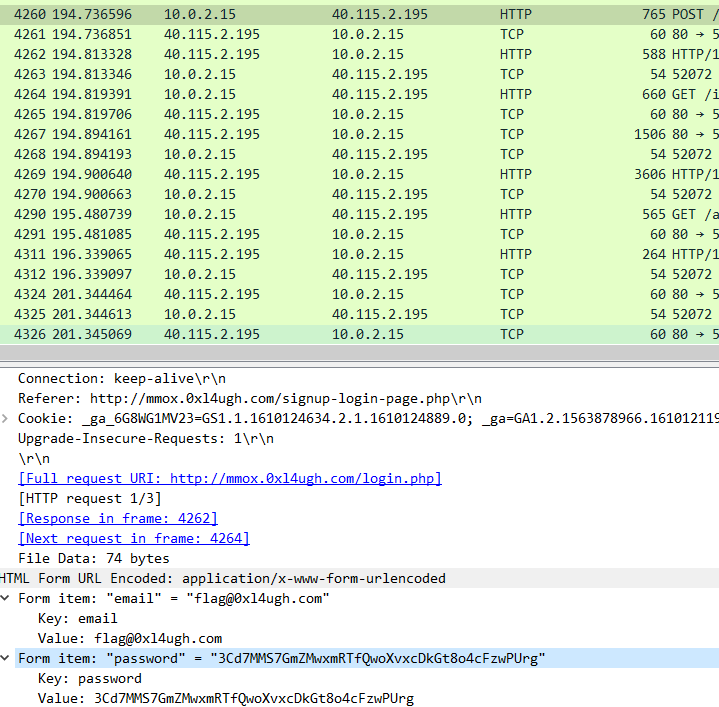
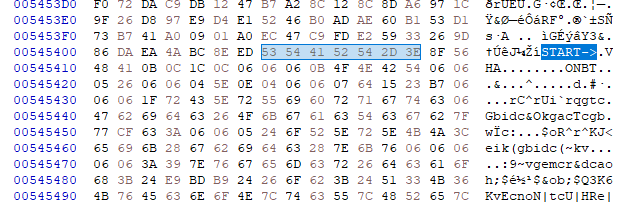
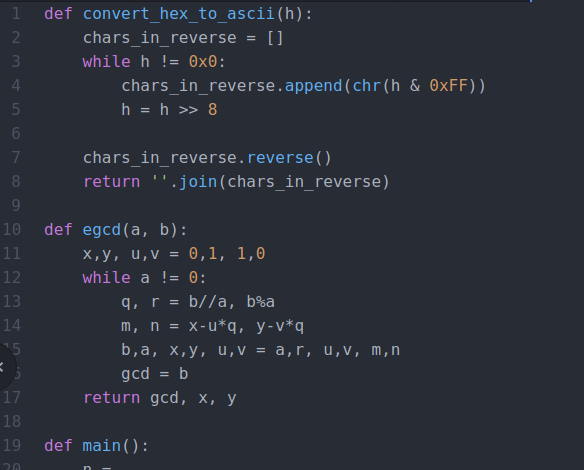
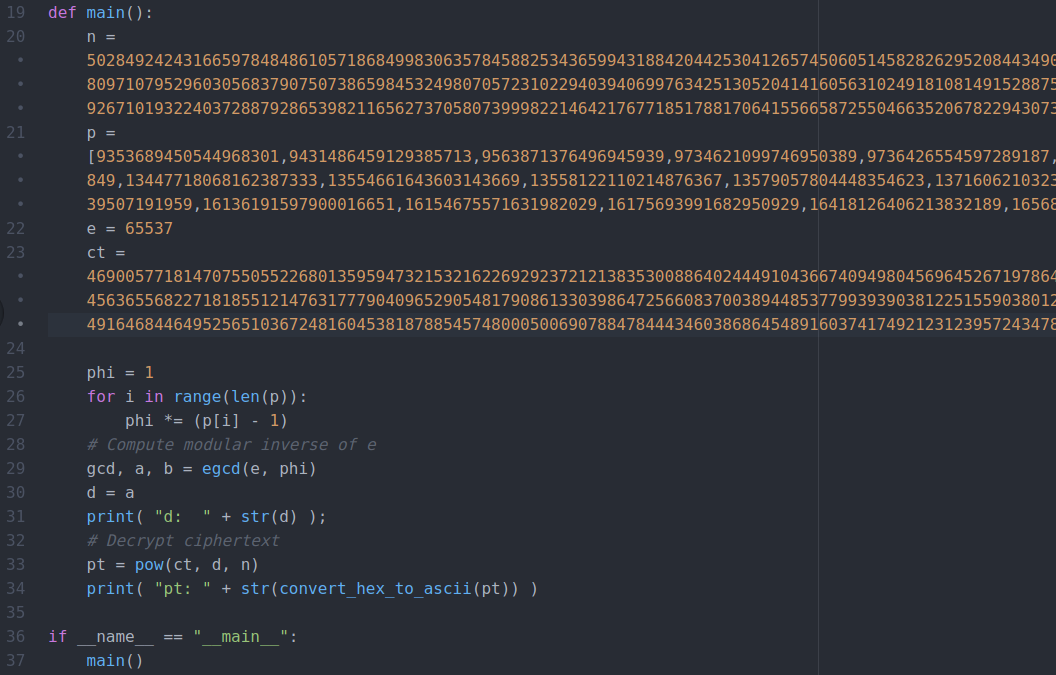
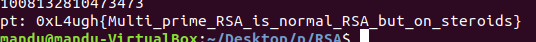
*CTF 2021
Crypto
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
from random import randint
import os
flag = "flag"
N=64
key=randint(0,2**N)
print key
key=bin(key)[2:].rjust(N,'0')
count=0
while True:
p=0
q=0
new_key=''
zeros=[0]
for j in range(len(key)):
if key[j]=='0':
zeros.append(j)
p=zeros[randint(0,len(zeros))-1]
q=zeros[randint(0,len(zeros))-1]
try:
mask=int(raw_input("mask:"))
except:
exit(0)
mask=bin(mask)[2:]
if p>q:
tmp=q
q=p
p=tmp
cnt=0
for j in range(0,N):
if j in range(p,q+1):
new_key+=str(int(mask[cnt])^int(key[j]))
else:
new_key+=key[j]
cnt+=1
cnt%=len(mask)
key=new_key
try:
guess=int(raw_input("guess:"))
except:
exit(0)
if guess==int(key,2):
count+=1
print 'Nice.'
else:
count=0
print 'Oops.'
if count>2:
print flag
|
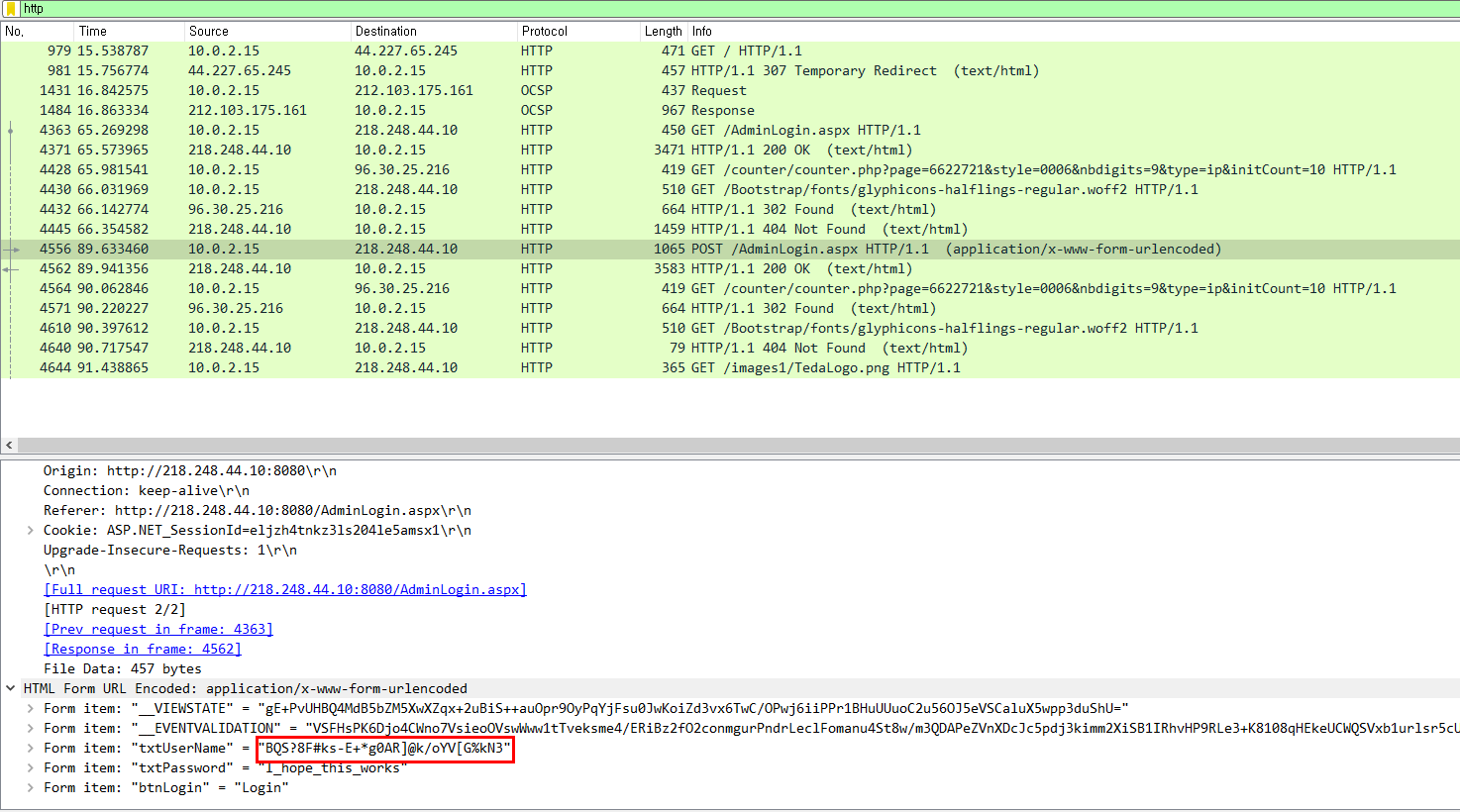
cs |
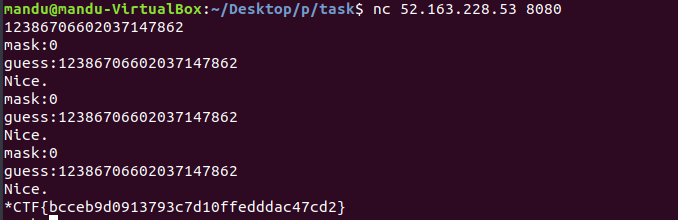
랜덤 key를 생성하고
generate random key
mask 값을 입력받아 여러번 xor을 해서
xor mask value and key
만들어진 key값을 3번 맞추면 되는데
need guessing key 3 times
mask에 0을 넣으면 xor을 몇 번을 하던지 그대로다.
however, when you put 0 in mask, xor calculation is useless.

|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
from random import randint
import os
from flag import flag
N=64
key=randint(0,2**N)
# print key
key=bin(key)[2:].rjust(N,'0')
count=0
while True:
p=0
q=0
new_key=''
zeros=[0]
for j in range(len(key)):
if key[j]=='0':
zeros.append(j)
p=zeros[randint(0,len(zeros))-1]
q=zeros[randint(0,len(zeros))-1]
try:
mask=int(raw_input("mask:"))
except:
exit(0)
mask=bin(mask)[2:]
if p>q:
tmp=q
q=p
p=tmp
cnt=0
for j in range(0,N):
if j in range(p,q+1):
new_key+=str(int(mask[cnt])^int(key[j]))
else:
new_key+=key[j]
cnt+=1
cnt%=len(mask)
key=new_key
try:
guess=int(raw_input("guess:"))
except:
exit(0)
if guess==int(key,2):
count+=1
print 'Nice.'
else:
count=0
print 'Oops.'
if count>2:
print flag
|
cs |
guesskey 문제 잘못냈나보다.
처음 print key가 주석처리되었다.
no print key :p
key를 2진법으로 나타냈을 때 0의 개수를 구해서
p와 q를 생성하고
p와 q번째 사이번째 비트는 mask와 xor을 하고
그 외 비트는 그대로 가져온다.
mask = 1 로 두고 계속 돌리면
하위 비트 쪽은 1로 되고
0의 개수가 작아지면서 p와 q도 작아지고
그럼 더더욱 하위 비트는 유지되고
just put 1 in mask.
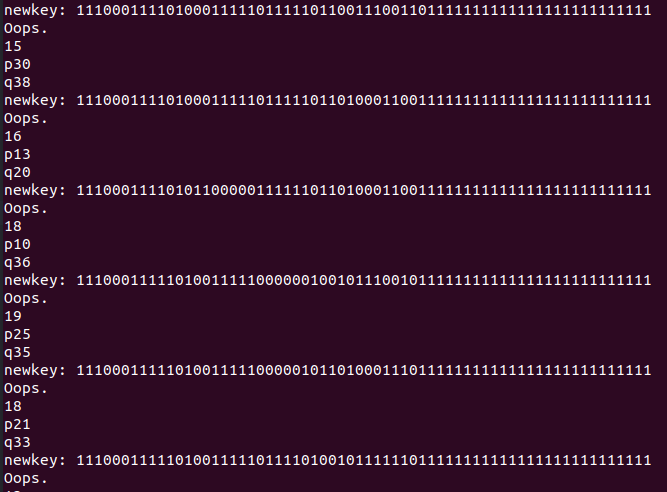
뭐 이런 식으로 비트들이 1로 되어간다.
it's gonna be 1s
한 150~200번 돌리면
try 150-200 times
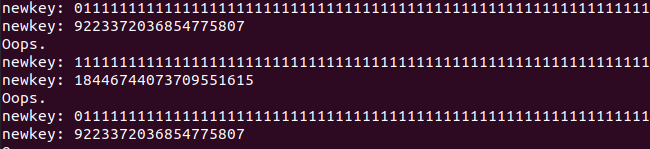
값은 두 개중 하나가 된다.
이제 mask = 0 으로 두고 두 개중 하나를 때려박으면 된다.
choice one between 92~ and 18~
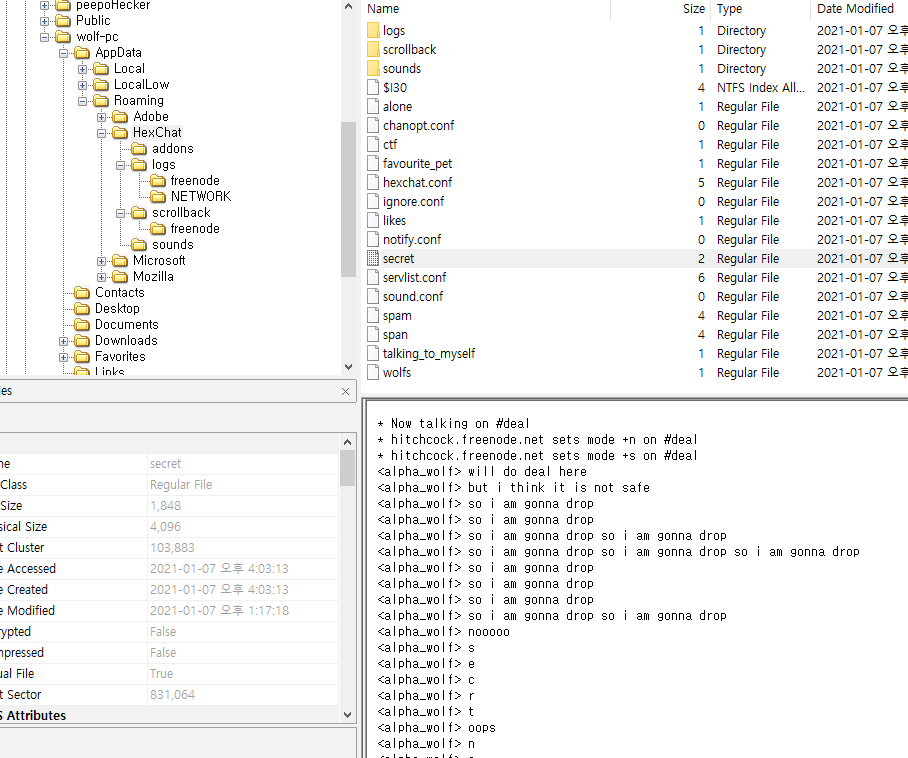
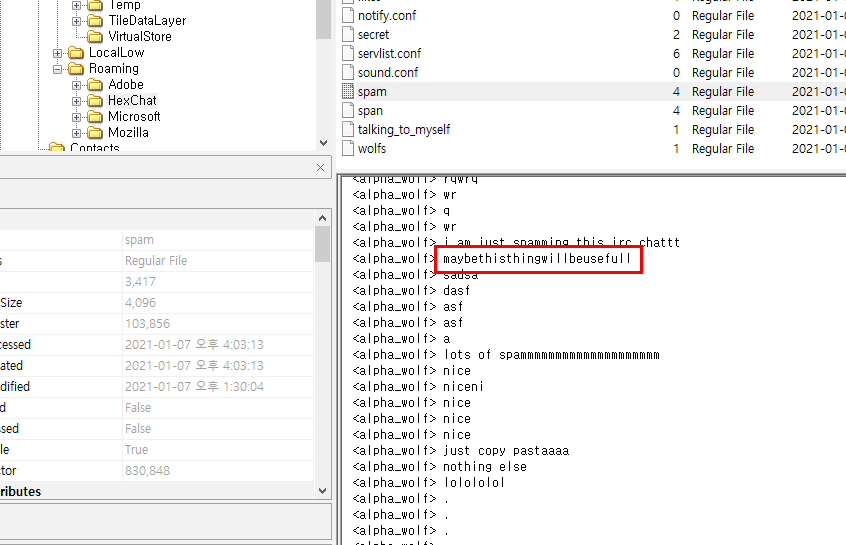
Misc

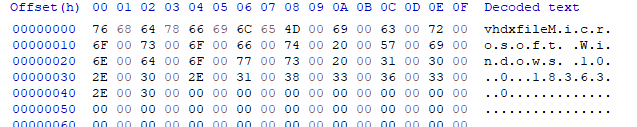
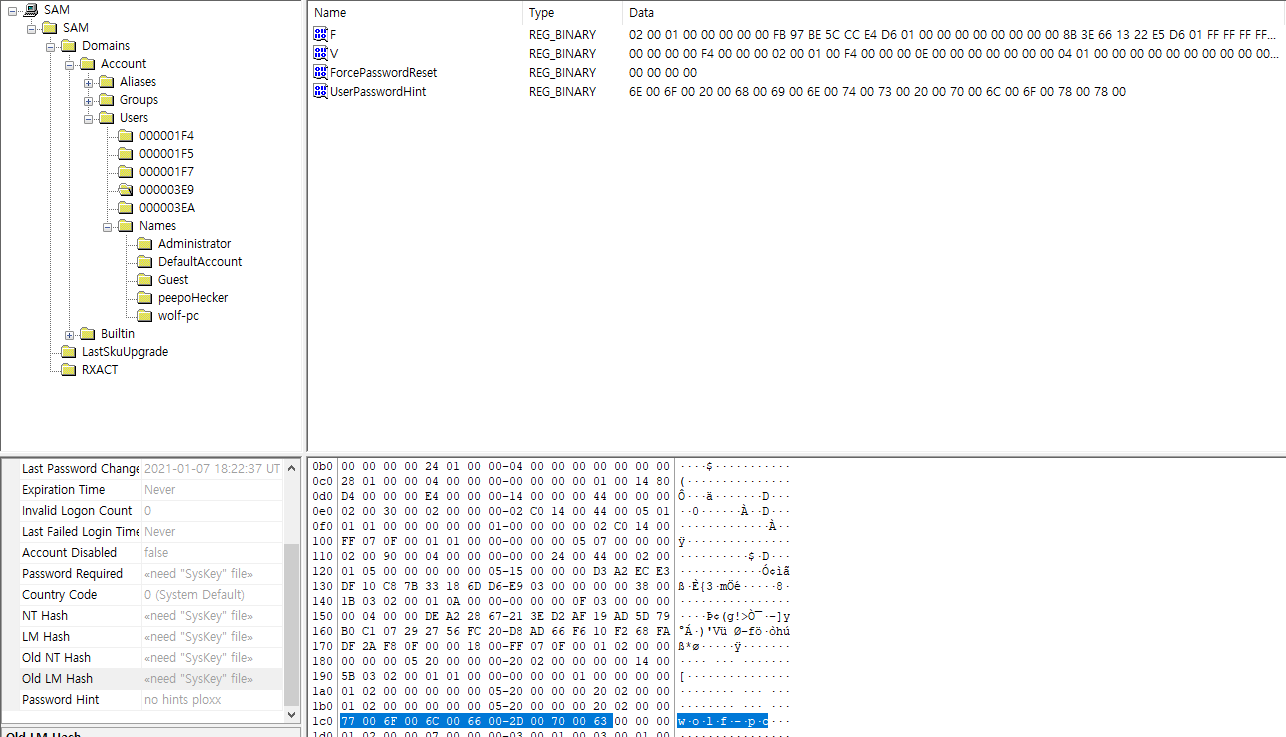
vhdxfile

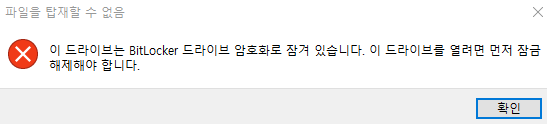
encrypted by BitLocker
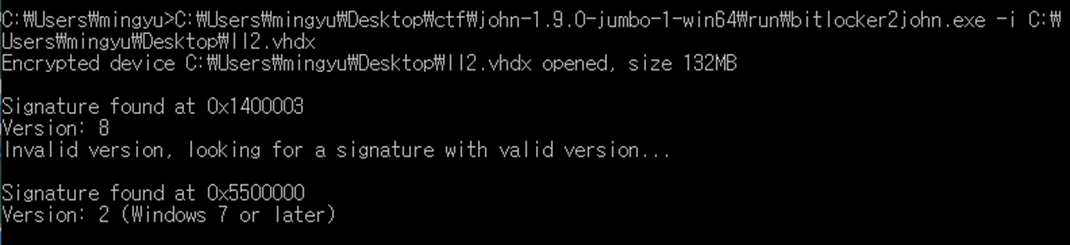
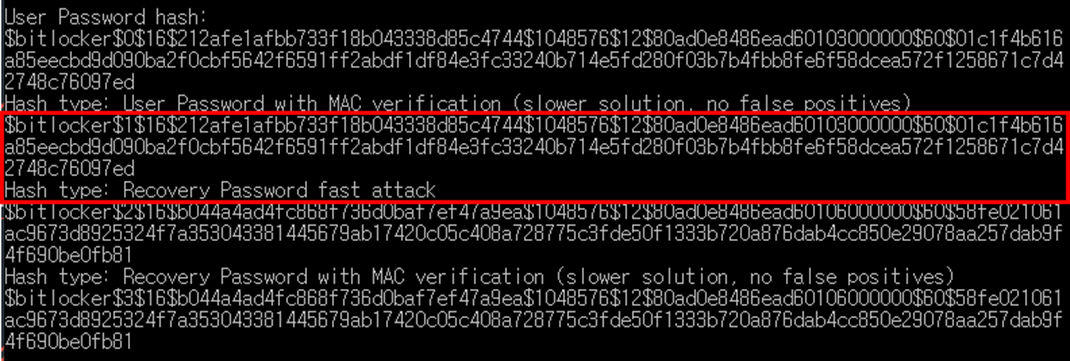
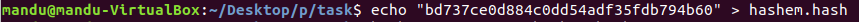
bitlocker2john

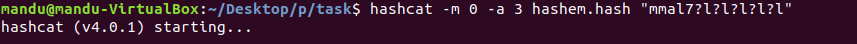
hashcat

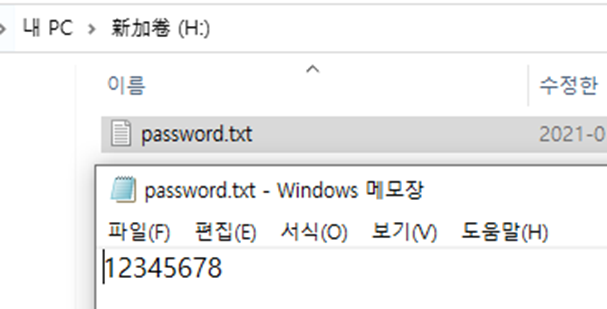
password 12345678
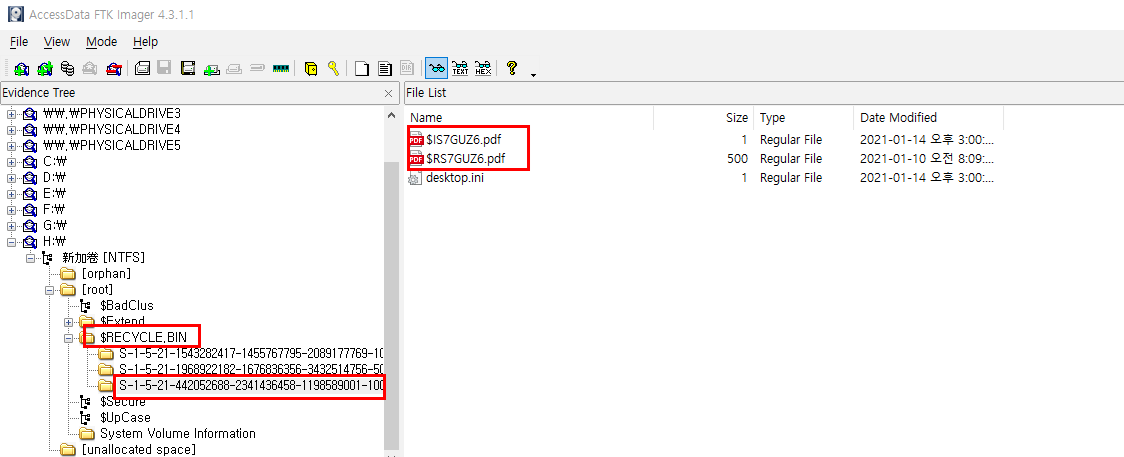
open with tool like ftk imager
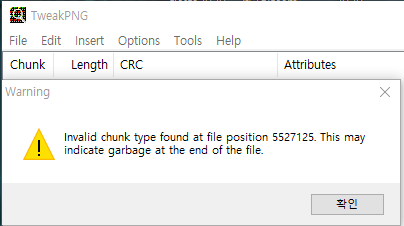
extract two pdf files
pdfcandy.com/extract-images.html
extract images from pdf files
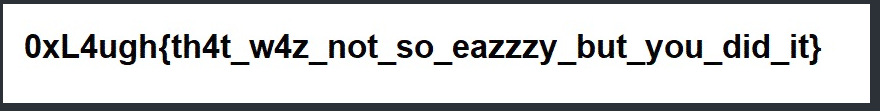
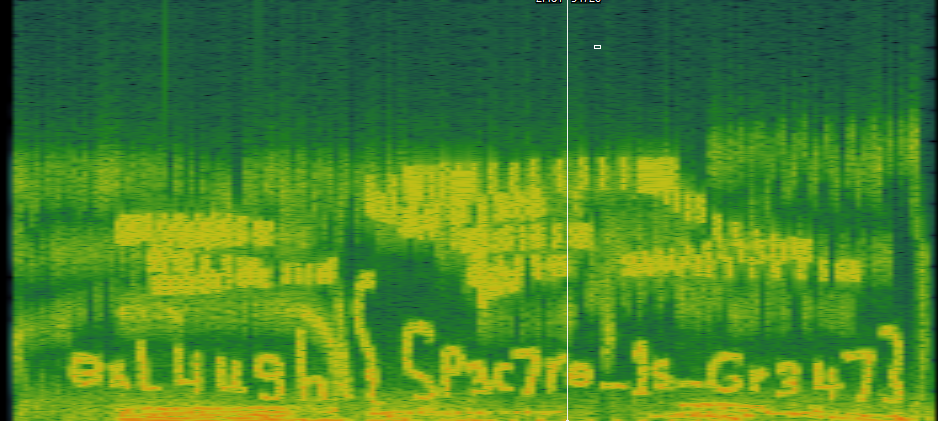
flag image. done.
'CTF Write Up' 카테고리의 다른 글
| 0x41414141 CTF Write up (0) | 2021.01.31 |
|---|---|
| ShadowCTF write up (0) | 2021.01.27 |
| The Cyber Grabs CTF 0x02 write up (0) | 2021.01.17 |
| 0xL4ugh CTF write up (0) | 2021.01.16 |
| 2020 Christmas CTF [show me the pcap] Write-up (2) | 2020.12.27 |