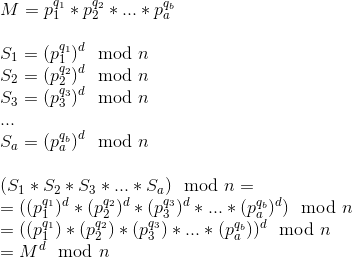
'cat flag' => 7161132565001953639 = 103 * 408479 * 170205956447


아래 Mars Rover 와 Remains 문제는 https://github.com/theori-io/ctf/blob/master/2021/SSTF2021/SSTF%202021%20The%20Duck%20-%20Write%20Up%20-%20rev%201.pdf 를 보고 푼 풀이를 작성하였습니다. (08.23)
Mars Rover
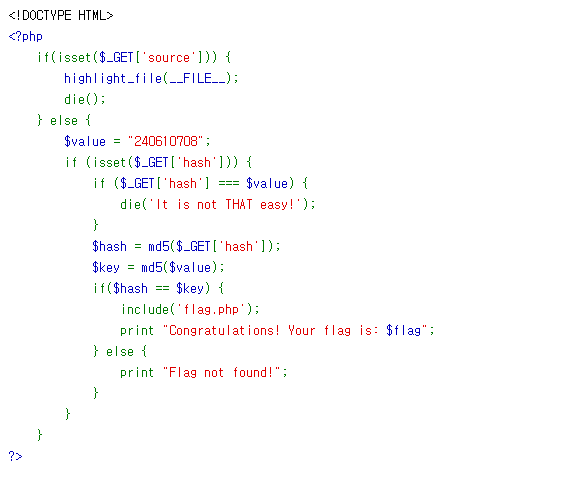
MarsRover.png 파일이 하나 주어진다.
파일을 살펴보면 2가지 특이사항이 있었다.
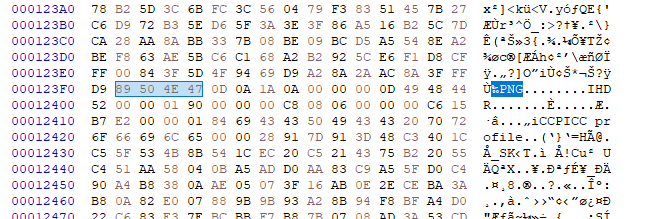
1. 이미지 양 옆 검은색 바 (stegsolve로 보았을 때)

2. TweakPNG로 청크를 확인했을 때, 일반적이지 않은 작고 여러개로 존재하는 IDAT 청크

풀이를 보니 이 중에서 2번째를 이용하는 것이었다.
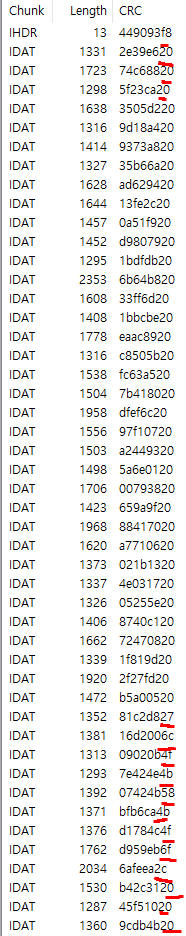
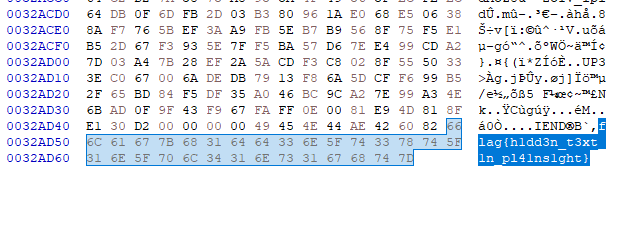
IDAT 청크의 CRC값의 마지막 1바이트가 ASCII범위의 값이다.
https://pyokagan.name/blog/2019-10-14-png/의 코드를 사용해서 해당 값을 추출하면 된다.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
import zlib
import struct
f = open('MarsRover.png', 'rb')
PngSignature = b'\x89PNG\r\n\x1a\n'
if f.read(len(PngSignature)) != PngSignature:
raise Exception('Invalid PNG Signature')
flag = ''
def read_chunk(f):
global flag
# Returns (chunk_type, chunk_data)
chunk_length, chunk_type = struct.unpack('>I4s', f.read(8))
chunk_data = f.read(chunk_length)
chunk_expected_crc, = struct.unpack('>I', f.read(4))
chunk_actual_crc = zlib.crc32(chunk_data, zlib.crc32(struct.pack('>4s', chunk_type)))
flag += chr(chunk_expected_crc & 0xff)
#if chunk_expected_crc != chunk_actual_crc:
# raise Exception('chunk checksum failed')
return chunk_type, chunk_data
chunks = []
while True:
chunk_type, chunk_data = read_chunk(f)
chunks.append((chunk_type, chunk_data))
if chunk_type == b'IEND':
break
print(flag)
|
cs |

Remains
주어진 Remains.zip을 열어보면 data 파일이 있다.
$file data로 7z 파일임을 알 수 있다. (간단하게 시그니쳐 확인해보면 된다.)
data.7z에 bin.sav 파일이 있다.
sav파일은 버츄얼박스 스냅샷으로 머신 상태를 저장했을 때 생기는 파일이다.
해당 파일을 뭘로 열어야 분석할 수 있을까..
관련 롸업을 찾아보면 됐다.
https://ox002147.gitlab.io/writeup-bitsctf-for60.html -> http://blog.rentjong.net/2014/05/asis-quals-2014-forensic-300.html -> https://www.dropbox.com/sh/vtsk0ji7pqhje42/AABY57lRqinlwZpo8t9zzGYka
savparser
Dropbox를 통해 공유함
www.dropbox.com
remains롸업에서도 해당 파일을 사용했다.
$gcc parsvbox.c lzf_d.c
$./a.out bin.sav
로 파싱 이후

readss.c의 코드에서 파일명 수정해주고
$gcc readss.c -o b.out
$./b.out
하면 out.raw파일이 생성됨. 해당 파일을 헥스에디터로 열어서 앞에 더미데이터를 지워주면 PNG로 열 수 있음.
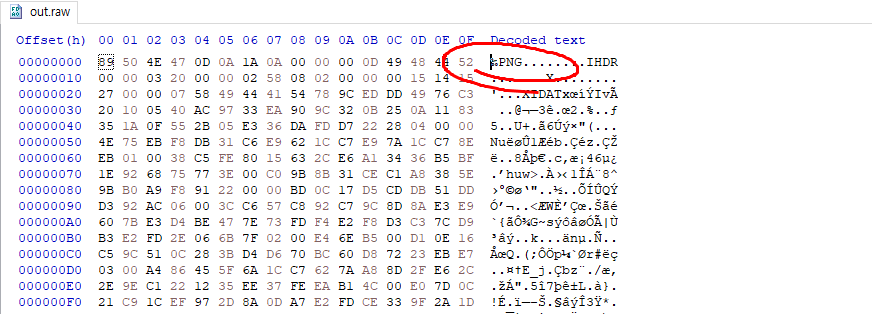

이러한 스샷 이미지를 얻을 수 있다.
./sav를 실행하고 Wanna flag? 라는 문자열이 출력된 것을 확인할 수 있다.

bin.sav-pgm.out 파일에서 해당 문자열을 찾을 수 있고
조금 내려보면 ELF 시그니쳐를 찾을 수 있다.
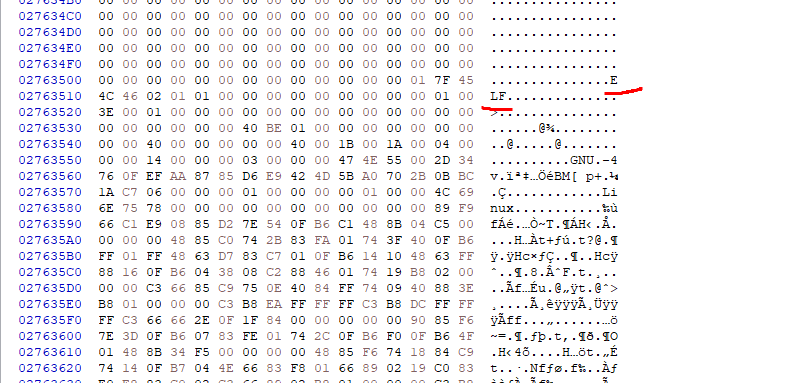
해당 바이너리를 추출해서 IDA로 열어서 리버싱으로 플래그를 찾아내면..
'CTF Write Up' 카테고리의 다른 글
| Fword CTF 2021 Forensics Write up (0) | 2021.09.25 |
|---|---|
| InCTF 2021 Forensics (0) | 2021.08.22 |
| RACTF 2021 Write up (0) | 2021.08.15 |
| RCTS CERT CTF 2021 write up (0) | 2021.08.11 |
| RTLxHA CTF 21 write up (0) | 2021.08.01 |